
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- HANA XSA log4j CVE-2021-44228
Technology Blogs by Members
Explore a vibrant mix of technical expertise, industry insights, and tech buzz in member blogs covering SAP products, technology, and events. Get in the mix!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
jgleichmann
Active Contributor
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-14-2021
10:31 AM
last updated: 2022-03-10 10:20 CET
Currently the security topic log4j (CVE-2021-44228 - CVSS score 10 of 10 and also others) is omnipresent. I want to show in this blog how you can check your HANA XSA systems and implement the mitigation. As well as to check if the settings are correct.

Source: GovCERT.ch
| The fix which should be provided by log4j version 2.15.0 is inclomplete in certain non default configurations - so a new CVE raised: CVE-2021-45046 (initial CVSS score 3,7 - now 9,0 / 10) This one will be fixed with log4j 2.16.0 Details: lunasec |
| There is a new vulnerability called CVE-2021-45105 rated with a CVSS of 7,5. This one will be fixed with log4j 2.17.0 which is now included in the latest XSA runtime version 1.0.142. |
| There is another new vulnerability called CVE-2021-44832 rated with a CVSS of 6,6. This one will be fixed with log4j 2.17.1 which is now included in the latest patch XSA runtime version 1.0.143 and XSA Cockpit 1.1.26. |
Overview
| CVE | effect | fixed by log4j version | CVSS score | mitigation via WA available | Release date |
| CVE-2021-44228 | execute arbitrary code loaded from LDAP servers | 2.16.0 | 10 | X | 20211126 |
| CVE-2021-45046 | remote code execution in some environments + local code execution | 2.16.0 | 9 | X | 20211214 |
| CVE-2021-45105 | stack overflow / DOS - denial of service | 2.17.0 | 7,5 | X | 20211216 |
| CVE-2021-44832 | remote code execution (RCE) attack | 2.17.1 | 6,6 | - | 20211211 |
To query the CVE database for all log4j vulnerabilities use this link for searching.
Overall currently affected products by SAP can be identified by using this document. It will be updated constantly. Last update is from 2022/03/09 15:55 EST (thanks to Kuto Baran for the hint)
There is a new central note for an overview (thanks to Matthias Sander for the hint):
3131047 - [CVE-2021-44228] Central Security Note for Remote Code Execution vulnerability associated ...
| Hint: Mark the note as favorite (star in the upper right corner) to get notified for any update on it. |
To mention some popular once:
- Cloud connector is not affected (Note: 3130868)
- BusinessObjects is not affected (Note: 3129956) - This applies to all the SAP BI products listed in the Environment section of the above mentioned document
- SAP NetWeaver Application Server Java is not impacted by the CVE-2021-44228, CVE-2021-45046 & CVE-2021-45105. This applies to all the AS Java Core Components. Applications running on top of it using the libs can be affected! (Note: 3129883)
- SAP NetWeaver Process Integration is affected (Note: 3131436/ 3130521)
- BTP Cloud Foundry applications can be affected (Note: 3130476 / 3131208)
Mitigation CVE-2021-44228
Log4j 1.x mitigation: Log4j 1.x is not impacted by this vulnerability.
Log4j 2.x mitigation: Implement one of the mitigation techniques below.
- Java 8 (or later) users should upgrade to release 2.16.0.
- Users requiring Java 7 should upgrade to release 2.12.2 when it becomes available (work in progress, expected to be available soon).
- Otherwise, remove the JndiLookup class from the classpath: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
Other insufficient mitigation measures are: setting system property log4j2.formatMsgNoLookups or environment variable LOG4J_FORMAT_MSG_NO_LOOKUPS to true for releases >= 2.10, or modifying the logging configuration to disable message lookups with %m{nolookups}, %msg{nolookups} or %message{nolookups} for releases >= 2.7 and <= 2.14.1.
The reason these measures are insufficient is that, in addition to the Thread Context attack vector mentioned above, there are still code paths in Log4j where message lookups could occur: known examples are applications that use Logger.printf("%s", userInput), or applications that use a custom message factory, where the resulting messages do not implement StringBuilderFormattable. There may be other attack vectors.
Source: Apache
Log4jscanner
There is a commandline tool (build via Go package) for scanning and rewriting / actively remove the vulnerable class from detected JARs in-place. You can use the git repository for further details.
XS Advanced applications
As we can see from the note the following HANA systems are affected:
- XSA
- HANA Cockpit (which also is running as XSA application) - see also note 3131397
XSA runtime affected: Version <= 1.0.140 (currently - 2021/12/21 - there is a now a new version 1.0.141 which includes a fix 3130864 - EXTENDED APPLICATION SERVICES 1 Release Collection 1.0.141! It includes log4j version 2.16.0) [thanks to Matthias Sander and sander.meijer3 ]
Determine XSA Runtime version
Login as sidadm:
xs version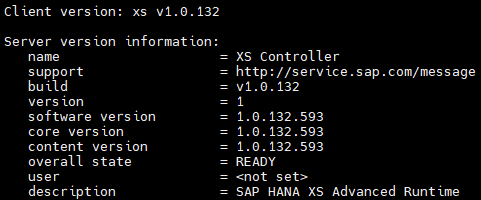
Check if you can implement the mitigation parameters with version >= 2.10
Determine log4j version
find /hana/shared/<SID>/xs/uaaserver/tomcat -name "*log4j*"
| XSA Advanced Runtime | log4j version | affected by | highest CVSS rating |
| <1.0.140 | <2.15 | CVE-2021-44228, CVE-2021-45046, CVE-2021-45105 | 10 |
| 1.0.141 | 2.16.0 | CVE-2021-45105 | 7,5 |
| 1.0.142 | 2.17.0 | CVE-2021-44832 | 6,6 |
| 1.0.143 | 2.17.1 | - | - |
Download patch search:
https://launchpad.support.sap.com/#/softwarecenter/template/products/%20_APP=00200682500000001943&_E...
There is a patch for HANA Cockpit SP14 Patch 6 from RTC 2022/03/02 which includes the XS Advanced Runtime 1.0.143. (Summary SP14)
The on-premise stack contains:
LCM for Cockpit - 2.5.61
HDB - 2.00.059
SAP_EXTENDED_APP_SERVICES - 1.0.143
XSAC_HRTT - 2.14.220501
XSAC_COCKPIT- 2.14.6
XSAC_PORTAL_SERV - 2.006.1
XSAC_XSA_COCKPIT - 1.1.26
Thanks to joerg.latza for posting the details.
Determine XSA Cockpit version
xs spaces
xs login -s <SPACE>
xs lc
| XSA COCKPIT version | log4j version | affected by | highest CVSS rating |
| <1.1.23 | <2.15.0 | CVE-2021-44228, CVE-2021-45046, CVE-2021-45105 | 10 |
| 1.1.23 | 2.15.0 | CVE-2021-45046, CVE-2021-45105 | 9 |
| 1.1.24 | 2.16.0 | CVE-2021-45105 | 7,5 |
| 1.1.25 | 2.17.0 | CVE-2021-44832 | 6,6 |
| 1.1.26 | 2.17.1 | - | - |
Download patch search:
https://launchpad.support.sap.com/#/softwarecenter/search/XSA%2520COCKPIT%25201
Attention From the note: On SAP HANA systems with enabled System Replication (HSR), execute step 1 on the primary and all secondary systems. Executing steps 2-4 is required on the primary system, only. |
| Upgade/Update issue If you installed HANA cockpit as well, it is not recommended to upgrade XSA Cockpit separately. Source: 3134932 - XSA Cockpit update fails with error "Selected component SAP HANA Cockpit Stack is not comp... Credits to Matthias Sander for the hint. |
Current information status is that all java version are affected. Also with deactivated class com.sun.jndi.ldap.object.trustURLCodebase .
>> It was initially reported by Lunasec that servers running on JDKs versions higher than 6u211, 7u201, 8u191 are not affected by the LDAP RCE attack vector, as the com.sun.jndi.ldap.object.trustURLCodebase is disabled by default, hence JNDI cannot load a remote codebase using LDAP. However, further analysis by the community has revealed that all JDK versions are vulnerable to this kind of attack. Alvaro Muñoz commented on Twitter the deserialization attacks are still possible with the latest JDK: "The ldap server will return a serialized object which will get deserialized. RCE depends on gadget availability in the classpath though" <<Source: https://www.infoq.com/news/2021/12/log4j-zero-day-vulnerability/
Check the used java version:
cd /hana/shared/<SID>/xs/sapjvm_*/bin
./java -version
Implementation of the parameters
login as sidadm
cdcoc
cp -p xsuaaserver.ini xsuaaserver.ini.bkp
cat xsuaaserver.ini
#if only the section [configuration] is available (default):
echo "UAA.Jvm.AdditionalParameters = -Dlog4j2.formatMsgNoLookups=true" >> xsuaaserver.ini
cat xsuaaserver.ini
#if not, insert the line via vi
vi xsuaaserver.inicheck your XSA before you apply changes:
XSA diagnose
XSA backup-ssfs
XSA backup-fssTo find vulnerable XS advanced applications with respect to CVE-2021-44228:
xs-admin-login
xs find-artifacts -n "log4j-core*"mitigations - note that due other CVE's than CVE-2021-44228 that an update is strongly recommended:
- set workaround environment parameter LOG4J_FORMAT_MSG_NO_LOOKUPS to true
- remove the JndiLookup class from the classpath
xs-admin-login
xs urevg --add LOG4J_FORMAT_MSG_NO_LOOKUPS true
cdxs
zip -q -d ./uaaserver/tomcat/webapps/uaa-security/WEB-INF/lib/log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
zip -q -d ./uaaserver/tomcat/webapps/uaa-security-oidc/WEB-INF/lib/log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
XSA restart| !!!This will restart your XSA services which means your applications will not be available for 15-30min!!! |
check xsuaaserver.out for the correct variables / parameters:
cdtrace
grep -i log4j xsuaaserver.out
as mentioned by sathiyaraj.jagadesh2 you can also check the parameters via revg:
xs revg | grep -i log4j
Check after implementation
XSA diagnose
Check the output in the trace directory: /hana/shared/<SID>/<hostname>/trace/xsa_diagnose_results.txt
As soon as there are updates on this topic I will update the blog.
I would wish SAP could list the components and versions of each patch. Having this information would save any customer a lot of time trying to figure out the right patch levels. Currently, these details are not published in any note or document. Nowadays it should not be impossible to provide such details.
SAP Security Patch Day - December 2021
https://wiki.scn.sap.com/wiki/display/PSR/SAP+Security+Patch+Day+-+December+2021
https://securitybridge.com/sap-patchday/sap-security-patch-day-december-2021/
Further sources:
https://logging.apache.org/log4j/2.x/security.html
https://www.govcert.ch/blog/zero-day-exploit-targeting-popular-java-library-log4j/
https://www.infoq.com/news/2021/12/log4j-zero-day-vulnerability/
https://support.sap.com/content/dam/support/en_us/library/ssp/my-support/trust-center/sap-tc-01-5025...
https://www.lunasec.io/docs/blog/log4j-zero-day-severity-of-cve-2021-45046-increased/
https://github.com/google/log4jscanner
- SAP Managed Tags:
- SAP HANA,
- SAP HANA, platform edition
43 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
"TypeScript" "Development" "FeedBack"
1 -
505 Technology Updates 53
1 -
ABAP
23 -
ABAP API
1 -
ABAP CDS Views
6 -
ABAP CDS Views - BW Extraction
3 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
3 -
ABAP DDIC CDS view
1 -
ABAP Development
6 -
ABAP in Eclipse
3 -
ABAP Platform Trial
1 -
ABAP Programming
3 -
abap technical
1 -
abap to xml
1 -
abapGit
1 -
absl
2 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
3 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
Advanced formula
1 -
Advanced Workflow
1 -
AEM
1 -
AI
9 -
AI Launchpad
2 -
AI Projects
1 -
AIML
11 -
AL11
1 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytic Models
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
5 -
API Call
2 -
API security
1 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Architecture
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
8 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
2 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
2 -
Artificial Intelligence role in shaping the future of Energy Industry
1 -
AS Java
1 -
ASE
1 -
ASR
2 -
Asset Management
2 -
Associations in CDS Views
1 -
ASUG
1 -
Attachment Handling. Create Attachment
1 -
Attachments
1 -
Authentication
1 -
Authorisations
1 -
Authorizations
1 -
Automate the Interim Account Update rule using Integration Center Job (Time Off)
1 -
Automated Test
1 -
Automating Processes
1 -
Automation
2 -
aws
2 -
Azure
2 -
Azure AI Studio
2 -
Azure API Center
1 -
Azure API Management
1 -
B2B Integration
1 -
Background job
1 -
Backorder Processing
1 -
Backpropagation
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
Bank Communication Management
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
batch
1 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
BI
1 -
bitcoin
1 -
Blockchain
3 -
bodl
1 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
21 -
BTP AI Launchpad
1 -
BTP Destination
2 -
BTP for Sustainability
1 -
BTP Scheduler
1 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Application Studio
3 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
2 -
Business Data Fabric
3 -
Business Fabric
1 -
Business Partner
14 -
Business Partner Master Data
13 -
Business Technology Platform
2 -
Business Trends
4 -
Business_catalog
1 -
BW ODP
1 -
BW4 HANA Dev
1 -
BW4HANA
1 -
C4C cloud root certificate
1 -
CA
1 -
calculation view
1 -
CAP
6 -
CAP development
1 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
13 -
CDS
3 -
CDS Views
1 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
ChatGPT
4 -
CICD
1 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
2 -
Cloud Extensibility
1 -
Cloud Foundry
4 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
Collaboration
1 -
Collaborative Draft
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation
1 -
Consolidation Extension for SAP Analytics Cloud
4 -
Control Indicators.
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Corrective Maintenance
1 -
Cosine similarity
1 -
CPI
3 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Custom Headers
1 -
Custom Integration
1 -
Custom Widget
2 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
cyber security
6 -
cybersecurity
1 -
DAC
1 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analysis
1 -
Data Analytics
2 -
Data and Analytics (DA)
2 -
Data Archiving
1 -
Data Back-up
1 -
Data Flow
1 -
Data Governance
6 -
Data Integration
2 -
Data Quality
13 -
Data Quality Management
13 -
Data Replication
1 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
9 -
Database
1 -
Database and Data Management
1 -
database tables
1 -
Databricks
1 -
Dataframe
1 -
Datasphere
7 -
Datasphere Delta
1 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debug
1 -
Debugging
2 -
Defender
1 -
Delimiting Pay Components
1 -
Delta Integrations
2 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing Fiori Elements
1 -
Developing with SAP Integration Suite
2 -
Devops
1 -
digital transformation
1 -
Disaster Recovery
1 -
Document Information Extraction
1 -
Documentation
1 -
Dot Product
1 -
DOX
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
duration
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT
1 -
Eclipse ADT ABAP Development Tools
3 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Emergency Maintenance
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
2 -
Enterprise Asset Management
2 -
Entra
1 -
ESLint
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
2 -
Exploits
1 -
File System
1 -
File Upload
1 -
Filter
1 -
Fiori
17 -
Fiori App Extension
2 -
Fiori Elements
2 -
Fiori Launchpad
2 -
Fiori SAPUI5
15 -
first-guidance
2 -
Flask
2 -
FLP_APP_MANAGER
1 -
FLP_CONTENT_MANAGER
1 -
Fragment Forms
1 -
Fragment Forms using ABA[
1 -
FTC
1 -
Full Stack
9 -
Funds Management
1 -
gCTS
1 -
Gemini
1 -
GenAI hub
1 -
General
3 -
Generative AI
4 -
Getting Started
1 -
GitHub
11 -
Google cloud
1 -
Grants Management
1 -
groovy
2 -
GTP
1 -
HANA
6 -
HANA Cloud
3 -
hana cloud database
2 -
Hana Cloud Database Integration
2 -
HANA DB
2 -
Hana Vector Engine
1 -
HANA XS Advanced
1 -
HanaDB
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
9 -
HTML5 Application
1 -
Hyperlinks
1 -
ICCX
1 -
ico
1 -
Identity cards validation
1 -
idm
1 -
Impact of AI on Energy Industry's Future
1 -
Implementation
1 -
Improvement Maintenance
1 -
Infuse AI
1 -
Input Controls
1 -
input parameter
1 -
instant payments
1 -
Integration
4 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
Internal Table
1 -
IoT
2 -
Java
1 -
Java Script
1 -
JavaScript
2 -
JMS Receiver channel ping issue
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
Jobscheduler
1 -
joule
5 -
Journal Entries
1 -
Just Ask
1 -
Kafka
1 -
Kerberos for ABAP
10 -
Kerberos for JAVA
9 -
KNN
1 -
KYMA
1 -
Launch Wizard
1 -
Learning Content
3 -
Life at SAP
4 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
List Report App
1 -
Live Sessions
1 -
Loading Indicator
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
6 -
Machine learning using SAP HANA
1 -
Marketing
1 -
Master Data
3 -
Master Data Governance
1 -
Master Data Management
15 -
Maxdb
2 -
MDG
2 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
6 -
ML Model Development
1 -
MLFlow
1 -
Modeling in SAP HANA Cloud
9 -
Monitoring
3 -
MPL
1 -
MTA
1 -
Multi-factor-authentication
1 -
Multi-Record Scenarios
1 -
Multilayer Perceptron
1 -
Multiple Event Triggers
1 -
Myself Transformation
1 -
Neo
1 -
NetWeaver
1 -
Neural Networks
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
3 -
Object Store
1 -
OCR
1 -
ODATA
3 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
ODP
1 -
ODP connectivity
1 -
ODP to Datasphere
1 -
Onpremise
2 -
open source
2 -
OpenAI
1 -
OpenAI API
1 -
Optimized Story Experience
1 -
Oracle
1 -
Overhead and Operational Maintenance
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
Partner Built Foundation Model
1 -
PAS-C01
1 -
Pay Component Management
1 -
Performance Forms
1 -
Personal story
1 -
PGP
1 -
Pickle
1 -
pio
1 -
PLANNING ARCHITECTURE
1 -
Plant Maintenance
2 -
Plugin Attachment
1 -
PO Directory API
1 -
Popup in Sap analytical cloud
1 -
Postgresql
1 -
PostgrSQL
1 -
POSTMAN
1 -
Practice Systems
1 -
Prettier
1 -
Proactive Maintenance
1 -
Process Automation
3 -
Process Management
1 -
Product Updates
6 -
Product Updates
1 -
PSE
1 -
PSM
1 -
Public Cloud
1 -
Python
5 -
python library - Document information extraction service
1 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
Rapid Data Governance
2 -
RDG
1 -
React
1 -
Reactive Maintenance
2 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
Replication using Cloud Connector
1 -
Report Malfunction
1 -
report painter
1 -
research
1 -
Research and Development Custom Widgets in SAP Analytics Cloud
1 -
Resilience
1 -
REST
1 -
REST API
1 -
Retagging Required
1 -
RFC
1 -
RFID
1 -
Risk
1 -
Robots
1 -
rolandkramer
3 -
Rolling Kernel Switch
1 -
route
1 -
Route determination
1 -
Router Non-XML condition
1 -
rules
1 -
S4 HANA
3 -
S4 HANA ABAP Dev
1 -
S4 HANA Cloud
2 -
S4 HANA On-Premise
3 -
S4Hana
9 -
S4HANA Cloud
1 -
S4HANA_OP_2023
2 -
SAC
13 -
SAC PLANNING
10 -
SAC STORIES
1 -
SAN
1 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
2 -
SAP AI
1 -
SAP AI Core
11 -
SAP AI Launchpad
9 -
SAP Analytic Cloud
1 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
9 -
SAP Analytics Cloud for Consolidation
4 -
SAP Analytics cloud planning
1 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP API Management
1 -
SAP Application Lifecycle Management
1 -
SAP Application Logging Service
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BO FC migration
1 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BODS migration
1 -
SAP BPC migration
1 -
SAP BTP
28 -
SAP BTP Build Work Zone
3 -
SAP BTP Cloud Foundry
9 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Generative AI
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP BTPEA
1 -
SAP Build
12 -
SAP Build App
1 -
SAP Build Apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
5 -
SAP Build work zone
11 -
SAP Business AI
1 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
2 -
SAP CAP
3 -
SAP CDC
1 -
SAP CDP
1 -
SAP CDS VIEW
1 -
SAP Certification
1 -
SAP Cloud ALM
6 -
SAP Cloud Application Programming Model
2 -
SAP Cloud Integration
3 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
10 -
SAP Companion
1 -
SAP CPI
4 -
SAP CPI (Cloud Platform Integration)
3 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
12 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
4 -
SAP Fiori App Embedding
1 -
SAP Fiori Elements
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HANA Dev tools
1 -
SAP HANA PAL
1 -
SAP HANA Schemas and HDI Container
1 -
SAP HANA Vector
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
11 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP LAGGING AND SLOW
1 -
SAP learning
1 -
SAP Learning Class
2 -
SAP Learning Hub
1 -
SAP Master Data
1 -
SAP MDG
1 -
SAP mentor
1 -
SAP Mentors
1 -
SAP Odata
3 -
SAP on Azure
3 -
SAP PAL
1 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP PO to CPI Migration
1 -
SAP Prepackaged Content
1 -
sap print
1 -
SAP Process Automation
3 -
SAP Process Integration
3 -
SAP Process Orchestration
2 -
SAP Router
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
3 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP Sapphire
1 -
SAP STMS
1 -
SAP successfactors
3 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP Utilities
1 -
SAP-GUI
9 -
SAP-Login-PowerShell
1 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapfirstguidance
4 -
SAPHANAService
1 -
SAPIQ
2 -
sapmentors
1 -
saponaws
2 -
saprouter
1 -
SAPRouter installation
1 -
SAPS4HANA
1 -
SAPUI5
6 -
SAPUI5 Extensibility
1 -
schedule
1 -
Script Operator
1 -
Secure Login Client Setup
9 -
security
11 -
Selenium Testing
1 -
Self Transformation
1 -
Self-Transformation
1 -
SEN
1 -
SEN Manager
1 -
Sender
1 -
service
2 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
9 -
Singlesource
1 -
SKLearn
1 -
Skybuffer AI
1 -
Slow loading
1 -
SOAP
3 -
SOAP Web Service
2 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
2 -
sql script
1 -
SSL
10 -
SSO
9 -
Story2
1 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Platform
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
Syniti RDG
1 -
Synthetic User Monitoring
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technical_catalog
1 -
Technology Architecture
1 -
Technology Updates
15 -
Technology Updates
1 -
Technology_Updates
1 -
terraform
1 -
Testing
1 -
Threats
2 -
Time Collectors
1 -
Time Off
2 -
Time Sheet
1 -
Time Sheet SAP SuccessFactors Time Tracking
1 -
Tips and tricks
2 -
toggle button
1 -
Tools
1 -
Trainings & Certifications
2 -
Transformation Flow
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
Tricentis Test Automation for SAP
1 -
TypeScript
3 -
ui designer
1 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
UploadSetTable
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
2 -
Vector Engine
1 -
Vectorization
1 -
Visual Studio Code
1 -
VSCode
2 -
VSCode extenions
1 -
Vulnerabilities
1 -
Web SDK
1 -
Web Service Configuration
1 -
Webhook
1 -
where used
1 -
work zone
1 -
Workflow Management
2 -
workload
1 -
xml
2 -
xml to csv
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
Related Content
- ABAP Cloud Developer Trial 2022: My Experience in Technology Blogs by SAP
- HANA Design-Time HDI composite role in Technology Q&A
- Introducing new type of Data Access Control "Operator and Value" for SAP Datasphere in Technology Blogs by SAP
- Integrate SAP S/4 HANA Private Cloud to SAP Signavio Process Insights in Technology Q&A
- LOGON 770 in Technology Q&A
Top kudoed authors
| User | Count |
|---|---|
| 8 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 | |
| 2 |