
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Best Practice for SAML Offline generator and local...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
09-06-2021
3:39 PM
Dear SAP community,
In this blog posting we will share with you the best practice for SAML Offline generator and local keystore with SAP SuccessFactors.
SAP SuccessFactors has deprecated Basic Authentication as of B2011 release (2H 2020 announcement: Planned Retirement of HTTP Basic Authentication (SFAPI/ODATA API)).
Please notice that Basic Auth deprecation was postponed until further notice. You can view the updated schedules here = 2H 2020 announcement: Planned Retirement of HTTP Basic Authentication (SFAPI/ODATA API)
SAP SuccessFactors recommends Customers/ SAP SuccessFactors Software Partners to use OAuth2.0 for Data Integrations.
OAuth2.0 authentication mechanism is respected by SFAPI (CompoundEmployee API)/ ODataV2 / ODataV4 APIs in SAP SuccessFactors.
SAP SuccessFactors uses the terminology for Authorization token as “Assertion” (SAML2.0) and for Access token as “access_token” as followed in the RFC-7522 specification
Please refer to the Authentication Using OAuth 2.0 section in the SAP SuccessFactors HXM Suite OData API: Developer Guide (V2)
There are 3 ways to generate the SAML Assertion:
This blog provides the solution brief on the second option - Generating the SAML Assertion using SAML offline tool in a secure way.
As ODataV2 is the commonly used APIs by SAP SuccessFactors customers, the example is showcased on SFOData.User entity
SAP Recommends to use strong passwords (As per customer IT/Security team requirements) for securing keystore file. In the video for demo purposes a 3 char password has been shown (0 minute 54 seconds)
SAML offline generation has the following advantages:
Hope this sample could be helpful for you 🙂
We would like to give the credits for our colleague karthick.chandrasekaran (SAP SuccessFactors Product Advisory and Partner Success) for this content.
Cheers
Soliman
In this blog posting we will share with you the best practice for SAML Offline generator and local keystore with SAP SuccessFactors.
Preface:
SAP SuccessFactors has deprecated Basic Authentication as of B2011 release (2H 2020 announcement: Planned Retirement of HTTP Basic Authentication (SFAPI/ODATA API)).
Please notice that Basic Auth deprecation was postponed until further notice. You can view the updated schedules here = 2H 2020 announcement: Planned Retirement of HTTP Basic Authentication (SFAPI/ODATA API)
Solution Overview:
SAP SuccessFactors recommends Customers/ SAP SuccessFactors Software Partners to use OAuth2.0 for Data Integrations.
OAuth2.0 authentication mechanism is respected by SFAPI (CompoundEmployee API)/ ODataV2 / ODataV4 APIs in SAP SuccessFactors.
Generic OAuth2 flow:

SAP SuccessFactors uses the terminology for Authorization token as “Assertion” (SAML2.0) and for Access token as “access_token” as followed in the RFC-7522 specification
Please refer to the Authentication Using OAuth 2.0 section in the SAP SuccessFactors HXM Suite OData API: Developer Guide (V2)
There are 3 ways to generate the SAML Assertion:
- (Recommended) Use a third-party IdP that you trust. Refer to the documentation of that IdP for detailed instructions.
- Use the offline tool.
- Use SAP SuccessFactors IdP. Note that the SAML assertion is valid only for 10 minutes in this case.
This blog provides the solution brief on the second option - Generating the SAML Assertion using SAML offline tool in a secure way.
Solution Brief:
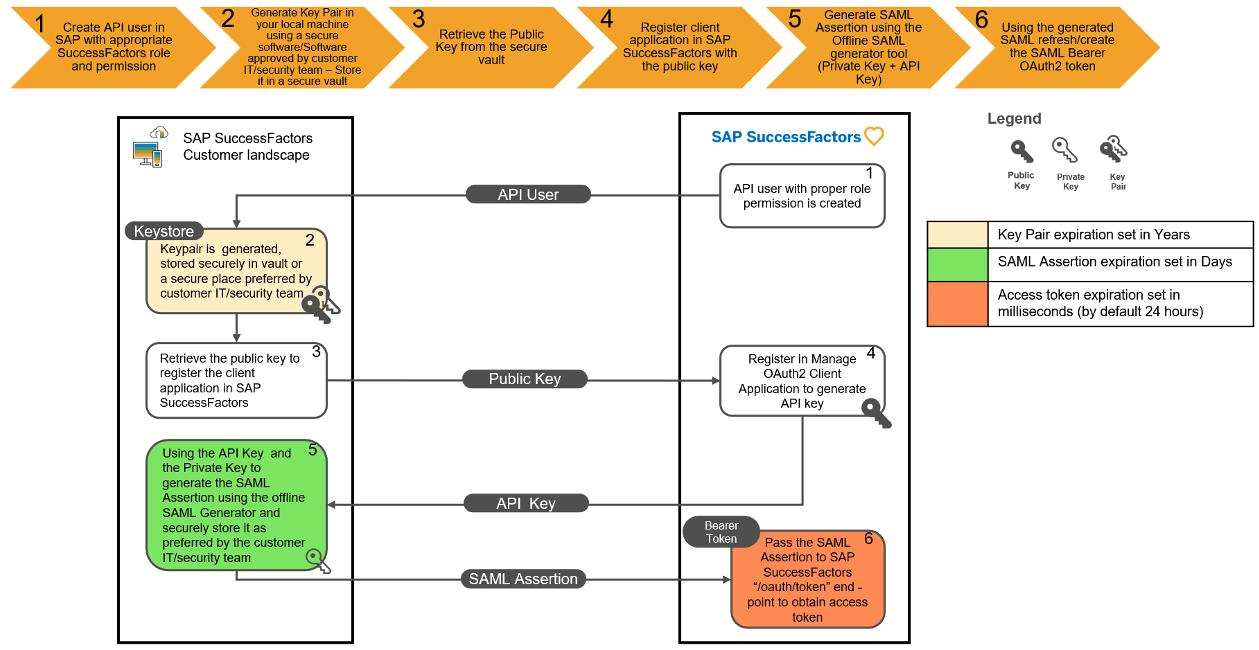
Disclaimers:
- In this video we have used a local key pair generation software for demonstration purposes, this is only to depict that SAP SuccessFactors can accept public keys from a 3rd party software (SAP does not recommend any specific key pair generation software, the customer IT/Security team must evaluate the tools available in the Enterprise segment and accordingly make the decision).
- The SAML offline tool used in this video is downloaded from SAP KBA 3031657
- While exporting the Private Key from the local key pair generation software, please do not encrypt it.
- For video purposes we have stored the Private key in a folder, SAP recommends that customers store the keys in secure vaults and keep it safe.
- For video purposes, user by the name “KC” is made up, and does not involve any specific integration scenario.
As ODataV2 is the commonly used APIs by SAP SuccessFactors customers, the example is showcased on SFOData.User entity
Consideration Points:
- Make sure to create Technical user for Data integrations, with only basic user data.
- Make sure the Role Based Permission assigned to the API user covers the intended target population and API permissions in SAP SuccessFactors.
- Key Pair will have an expiration time, generally in years. When the Key Pair expires accordingly make sure to re-register the client application using the new public key.
- SAP SuccessFactors supports both SHA-1 and SHA-2 signing algorithm.
- Please ensure that there are no spaces and no new line characters in the public key, while registering in the Manage OAuth2 client application screen of SAP SuccessFactors.
- SAML Assertion generated using the offline tool, will have expiration assigned in days (This is a parameter in the “SAMLAssertion.properties” file and can be set accordingly as per the Customer IT team policy for expiration).
- Once the SAML Assertion is expired, the respective Customer IT/Security team must regenerate the SAML assertion and share it with the Integration team.
- SAML Assertion is used to refresh the access token.
SAP Recommends to use strong passwords (As per customer IT/Security team requirements) for securing keystore file. In the video for demo purposes a 3 char password has been shown (0 minute 54 seconds)
Conclusion:
SAML offline generation has the following advantages:
- Control over the key pair life cycle – As the customer decides the expiration time
- Securing the private key
- SAML expiration time can be controlled as per customer IT/Security team policy
Hope this sample could be helpful for you 🙂
We would like to give the credits for our colleague karthick.chandrasekaran (SAP SuccessFactors Product Advisory and Partner Success) for this content.
Cheers
Soliman
- SAP Managed Tags:
- SAP Integration Suite,
- API,
- SAP SuccessFactors HXM Suite,
- Cloud Integration
Labels:
11 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
107 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
72 -
Expert
1 -
Expert Insights
177 -
Expert Insights
340 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
14 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,575 -
Product Updates
384 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,872 -
Technology Updates
472 -
Workload Fluctuations
1
Related Content
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
- Deliver Real-World Results with SAP Business AI: Q4 2023 & Q1 2024 Release Highlights in Technology Blogs by SAP
- New Partner Content on SAP Business Accelerator Hub (Q4 ’23) in Technology Blogs by SAP
- Talent Intelligence Hub and SAP SuccessFactors HXM Suite Integration as of Release 2H 2023 in Technology Blogs by SAP
- Extend the Power of Data for SAP RISE Customers: data federation with SAP in multi-cloud Azure in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 17 | |
| 14 | |
| 12 | |
| 10 | |
| 9 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 6 |