
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Connecting from SAP Business Application Studio to...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
tamir_menahem
Explorer
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-21-2021
8:36 AM
SAP Business Application Studio (BAS) is a modern development environment that enables you to develop various applications for various target platform runtimes, such as ABAP platform (on-premise and cloud), SAP BTP Cloud Foundry environment (CF), SAP HANA Cloud, and SAP Mobile Platform.
BAS itself is an SAP Business Technology Platform (BTP) service decoupled from these runtimes. In fact, it runs on a dedicated set of Kubernetes clusters.
While most of the development supported by BAS are targeted for CF, one might mistakenly think that connection to CF is mandatory for any scenario. This, of course, is not the case. BAS can be used without any relation to CF. If your target runtime is not CF, then you do not have to create a CF Org or Space, you do not have to be a CF Org or Space member, and you do not need to log in to CF to work with BAS. You only need to subscribe to the BAS service from your subaccount.
Now that we understand that BAS is a standalone development environment, let’s take a closer look at the ways in which you can connect to CF when you use BAS to develop CF applications.
Note: The following section describes how different identity management settings in your BTP subaccount influence the CF login process. However, all other CF operations, such as Set Org and Space, are the same when performed in BAS (regardless of the identity management settings).
BAS offers two ways to connect to CF:
Notes:
Now, as long as you keep the default identity management settings in your subaccount, things are quite straight forward. However, the difference between using the UI and CLI with regards to the CF login becomes more important when we consider the different Identity Providers (IdP).
Here are some key players in BTP Identity Management:
Notes:
The table below provides a comparison between the different CF IdPs for CF login in BAS:
Additional aspects to consider:
SAP ID Service
Note: For the SAP ID Service, you can perform this command from the Command Palette.
Custom IdP
Corporate IdP
Single command option:
This is it. I hope now you have a better understanding of the differentiation between BAS and CF, between Application IdP and CF IdP, between the different IdPs and their impact on the CF login procedure, and most important, that you successfully connected from BAS to CF.
BAS itself is an SAP Business Technology Platform (BTP) service decoupled from these runtimes. In fact, it runs on a dedicated set of Kubernetes clusters.
While most of the development supported by BAS are targeted for CF, one might mistakenly think that connection to CF is mandatory for any scenario. This, of course, is not the case. BAS can be used without any relation to CF. If your target runtime is not CF, then you do not have to create a CF Org or Space, you do not have to be a CF Org or Space member, and you do not need to log in to CF to work with BAS. You only need to subscribe to the BAS service from your subaccount.
Now that we understand that BAS is a standalone development environment, let’s take a closer look at the ways in which you can connect to CF when you use BAS to develop CF applications.
Note: The following section describes how different identity management settings in your BTP subaccount influence the CF login process. However, all other CF operations, such as Set Org and Space, are the same when performed in BAS (regardless of the identity management settings).
BAS offers two ways to connect to CF:
- UI-based, from the Command Palette

- CLI-based, from the Terminal
Notes:
- In both cases, the CF CLI is used, indirectly (UI-based) or directly (CLI-based), so that the specific target operation is achieved in both ways.
- The CF CLI usage from the BAS terminal is identical to that of the CF CLI in your local machine (e.g. laptop).
- The UI-based approach provides the best user experience, but typically, when you compare the UI and CLI approaches, you find that the CLI provides the full capabilities, while the UI (which is based on the given CLI) covers the common operations and not necessarily all the capabilities.
Now, as long as you keep the default identity management settings in your subaccount, things are quite straight forward. However, the difference between using the UI and CLI with regards to the CF login becomes more important when we consider the different Identity Providers (IdP).
Here are some key players in BTP Identity Management:
- Application IdP
- Relevant for business users.
- Serves for BAS login.
- Based on SAP Authorization and Trust Management Service.
- This is not relevant for CF login, but I am mentioning it here to avoid confusion.
- CF IdP
- Relevant for CF users.
- Serves for CF login.
- Based on CF UAA (User Account and Authentication).
- SAP ID Service (a.k.a. SAP Tenant)
- Default IdP.
- A pre-configured, easy-to-use global standard SAP public IdP (account.sap.com) that is shared by all customers.
- You cannot delete the SAP ID configuration, but you can add different IdPs (Custom IdP, or Corporate IdP) for customized user management.
- Custom IdP
- A tenant-specific Identity Authentication Service (IAS) with local users.
- Corporate IdP (a.k.a. External IdP)
- A tenant-specific IAS that acts as a proxy to your own IdP.
Notes:
- The Application IdP and the CF IdP can be set to the SAP ID Service, the Custom IdP, or the Corporate IdP separately, or you can set them to the same IdP.
- To add the CF IdP (currently supported in Feature Set A), Custom IdP, or Corporate IdP, you need to open a ticket using the BC-CP-CF-SEC-IAM component. There is no self-service.
The table below provides a comparison between the different CF IdPs for CF login in BAS:
| SAP ID Service | Custom IdP | Corporate IdP | |
| BAS UI-based login | Supported | Not supported | Not supported |
| BAS CLI-based login | Supported | Supported | Supported |
| CLI-based login example | Reference cf login | Reference cf login --origin <IdP Name> | Reference cf login --sso |
| Authorization flow | OAuth Resource Owner Password | OAuth Resource Owner Password | OAuth Authorization Code Grant (browser flow) + One-Time Passcode |
Additional aspects to consider:
- If you do not know the CF IdP origin (IdP Name) then you should contact your administrator. The CF IdP origin is also not being exposed in SAP BTP cockpit.
- Both the Custom IdP and the Corporate IdP require an origin to know which IdP is being used. For the Custom IdP, it can be done on the CLI level, while for the Corporate IdP, it must be done on the UI level (SAP BTP CF Login screen, outside of BAS). (UI level) settings should be defined for each browser that you use, and it is not supported in browser private mode (a.k.a. Incognito mode) since it is based on persistent cookies. This limitation is result of the CF UAA usage and improvement is expected.
- The Corporate IdP doesn’t support the OAuth Resource Owner Password (OAuth Password flow). Therefore, the OAuth Authorization Code Grant (browser flow) flow is mandatory (based on
cf login --sso). - The OAuth Authorization Code Grant + One-Time Passcode flow (based on
cf login --sso), can be used in all use cases (SAP ID Service, Custom IdP, Corporate IdP) and is a more secure way. - SSO is only supported in the browser flow (i.e. not supported OAuth Password flow).
- CF Login command:
cf login [-a API_URL] [-u USERNAME] [-p PASSWORD] [-o ORG] [-s SPACE] [--sso | --sso-passcode PASSCODE] [--origin ORIGIN]
Login Sample
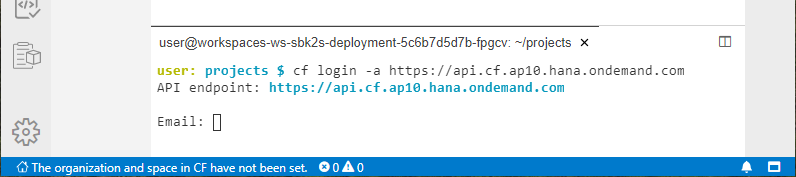
SAP ID Service
Note: For the SAP ID Service, you can perform this command from the Command Palette.
cf login -a https://api.cf.ap10.hana.ondemand.com
API endpoint: https://api.cf.ap10.hana.ondemand.com
Email: john.do@mycompany.com
Password:
Authenticating...
OKCustom IdP
cf login -a https://api.cf.ap10.hana.ondemand.com --origin <IdP Name>
API endpoint: https://api.cf.ap10.hana.ondemand.com
Email: john.do@mycompany.com
Password:
Authenticating...
OKCorporate IdP
cf login -a https://api.cf.ap10.hana.ondemand.com --sso
API endpoint: https://api.cf.ap10.hana.ondemand.com
Temporary Authentication Code ( Get one at
https://login.cf.ap10.hana.ondemand.com/passcode 😞 <Temporary Authentication Code, e.g. yF1e16KTjS>
Authenticating...
OK
Single command option:
cf login -a https://api.cf.ap10.hana.ondemand.com --sso-passcode <Temporary Authentication Code, e.g. yF1e16KTjS>
API endpoint: https://api.cf.ap10.hana.ondemand.com
Authenticating...
OKSummary
- BAS is a standalone development environment, decoupled from the target platform runtimes.
- You need to connect from BAS to CF when you develop CF applications.
- You connect to CF based on CF IdP, which is relevant for CF users, and not based on application IdP, which is relevant for business users and serves for BAS login.
- The way you login from BAS to CF, UI-based (Command Palette) or CLI-based (Terminal) using different parameters, depends on the identity management set up in your subaccount:
- SAP ID Service - UI or CLI (
cf login) - Custom IdP - CLI (
cf login --origin <IdP Name>) - Corporate IdP - CLI (
cf login --sso)
- SAP ID Service - UI or CLI (
This is it. I hope now you have a better understanding of the differentiation between BAS and CF, between Application IdP and CF IdP, between the different IdPs and their impact on the CF login procedure, and most important, that you successfully connected from BAS to CF.
- SAP Managed Tags:
- SAP Business Application Studio,
- SAP BTP, Cloud Foundry runtime and environment
Labels:
8 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
116 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
75 -
Expert
1 -
Expert Insights
177 -
Expert Insights
355 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
14 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,575 -
Product Updates
398 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,871 -
Technology Updates
491 -
Workload Fluctuations
1
Related Content
- SAP BTP ABAP Environment – Release 2405 in Technology Blogs by SAP
- Standard Single Host Installation of SAP ERP 6 EHP8 using Oracle DB 19c on Oracle Linux Host in Technology Q&A
- Develop with Joule in SAP Build Code in Technology Blogs by SAP
- Business AI for Aerospace, Defense and Complex Manufacturing in Technology Blogs by SAP
- Using Postgresql Database in Cloud Application Programming model in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 20 | |
| 11 | |
| 8 | |
| 8 | |
| 7 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 6 |