
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Exchange JWT token from Azure with token issued by...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content

Step 1 of the process involves making a request to Microsoft Azure application using either Resource Owner Password Credentials or Authorization Code flow. The end result of this process is that Azure AD will issue an ID token which we can use for token exchange. Few things to note for this to work:
- SAP Cloud Identity Authentication Service should be setup as an OIDC application in Microsoft Azure. This can be accomplished using this blog.
- Update the manifest file for Azure app to make sure accesstokenAcceptedVersion is set to 2.
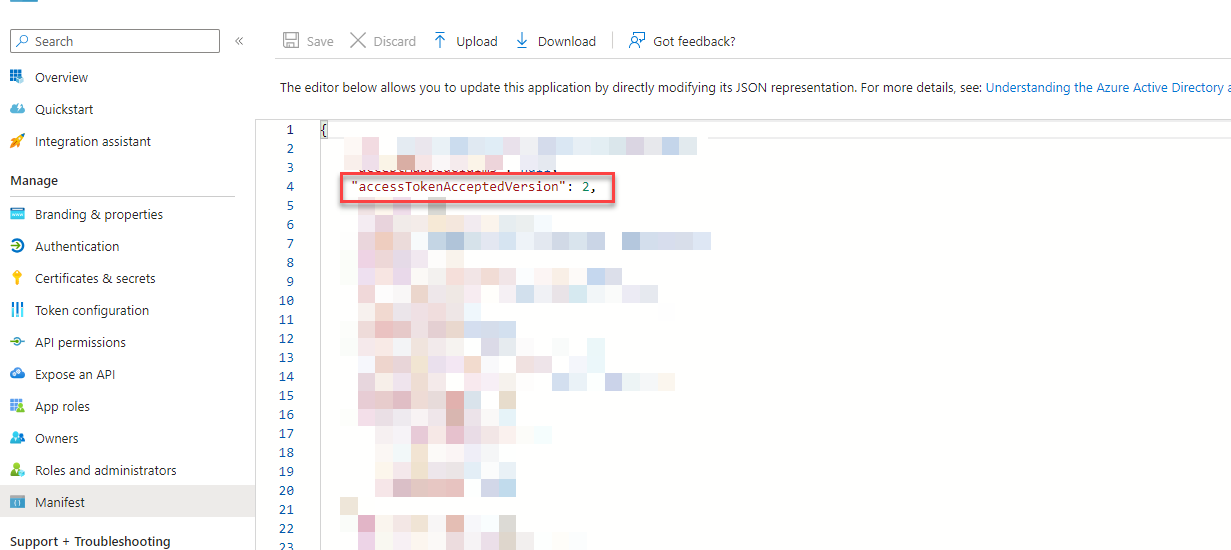
- Use the right token endpoint for Microsoft when making the token request from your client. It should be https://login.microsoftonline.com/{{tenantID}}/oauth2/v2.0/token. Make sure to retrieve the v2 of the token.
- ClientID used in the request should be for the SAP Cloud Identity Services application registered in MS Azure.
Here is screenshot of the request to MS Azure using Postman and retrieved token from Azure.

Decoding the ID token shows that the aud field is set to the clientID of the IAS application in Azure. Note that the token version is also set to 2.0. Both of these are necessary for SAP Cloud Identity Authentication Service to accept this token for a token exchange.
In Step 3, the Azure token can be exchanged for a token issued by IAS. To successfully do this exchange we need make sure that the issuer of the external corporate identity provider is configured as a corporate identity provider and set as a default identity provider or configured via Authentication Rules (Conditional Authentication) in the administration console for SAP Cloud Identity Services. In addition Client ID and Client Secret are also required to send the request.
To retrieve the information required for token exchange, follow the steps below:
- Access SAP Cloud Identity Authentication Service admin console using the URL: https://<iashostname>.accounts.ondemand.com/admin.
- Authenticate as an administrator user.
- Click Applications & Resources >> Applications and select your application. In my case I am selecting the app created when trust is established between BTP subaccount and IAS.
- Scroll down and click Conditional Authentication.
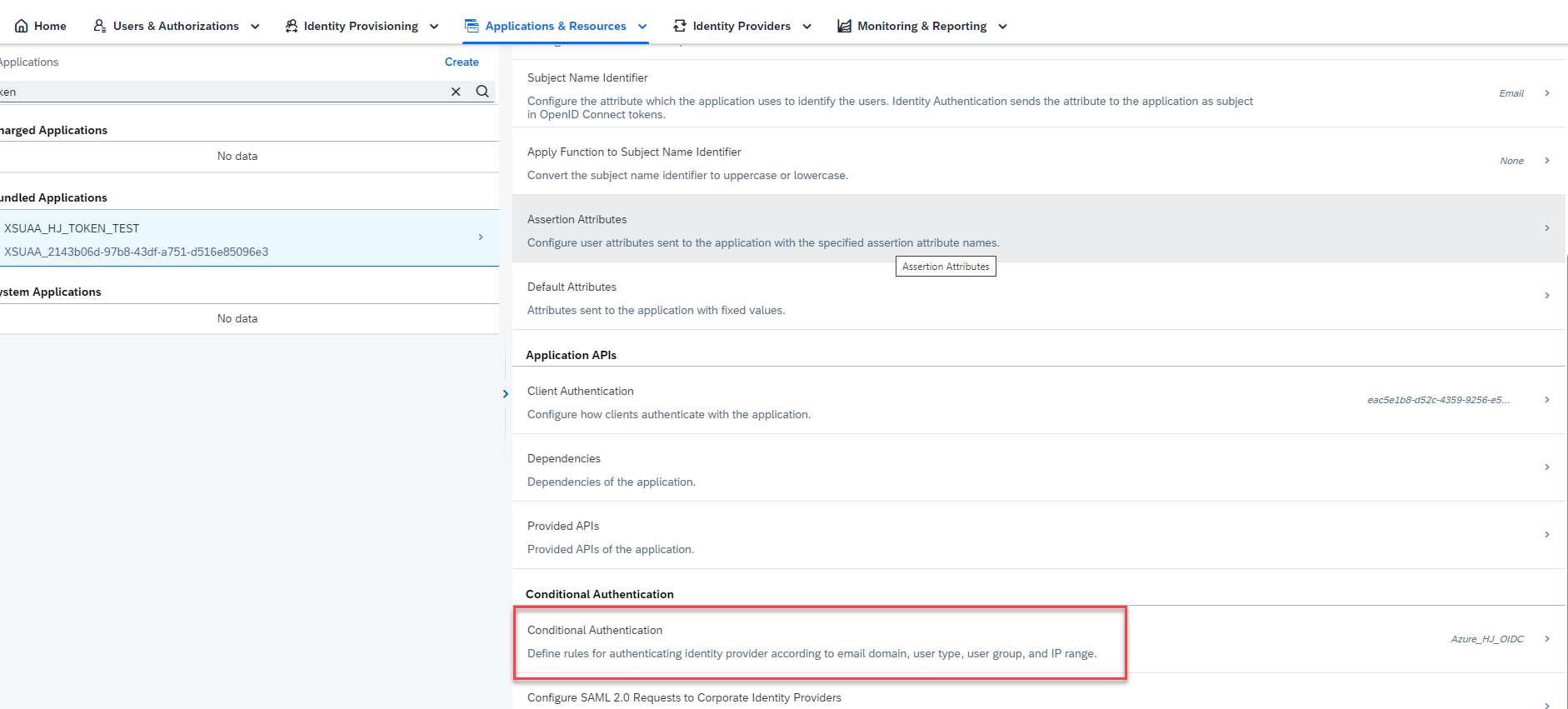
- Confirm that Azure is setup as the Default Identity Provider for your application. Alternatively, it's possible to leave the Default Identity Provider to Identity Authentication and set conditional rules to forward the request to Azure. For more information on setting up conditional rules, follow the help guide.
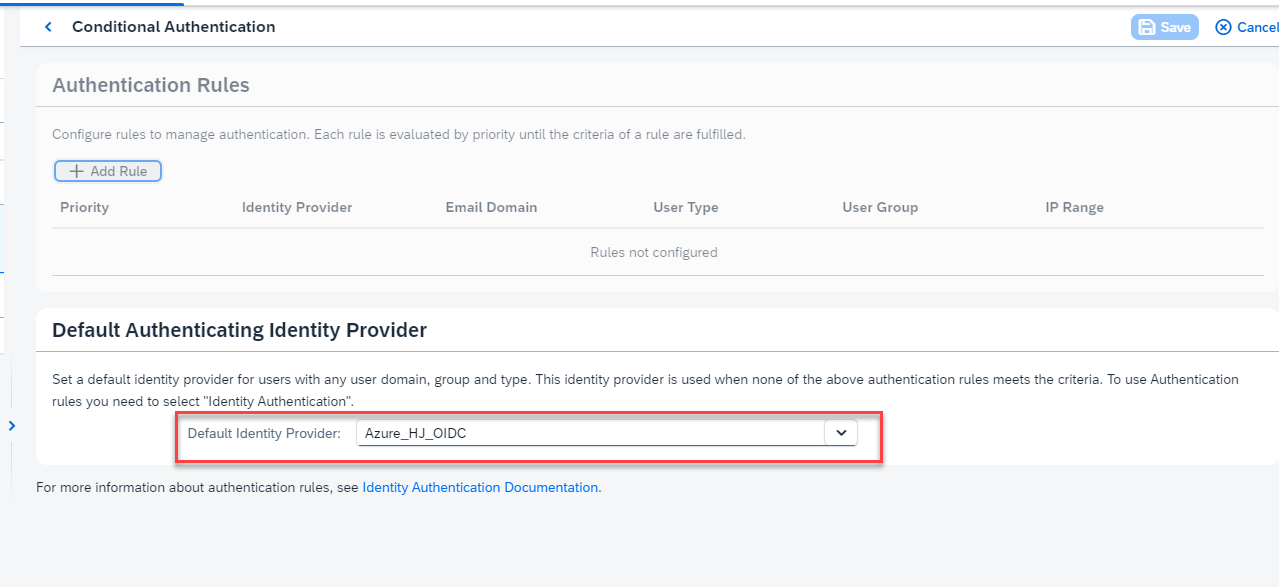
- Click the back arrow and click Client Authentication.

- Under Secrets, click +Add to add a new secret and click Save.

- Make note of the Client ID and Client Secret as that's required for API authentication and click OK.

We can now send the request to IAS for the token exchange. The request should be formulated using the following information:
- Token URL: https://<iashostname>.accounts.ondemand.com/oauth2/token
- Request Headers:
- Content-Type: application/x-www-form-urlencoded
- Authentication: Basic Authentication
- Body:
- assertion: <id token from retrieved from Azure in the previous request>
- grant_type: urn:ietf:params:oauth:grant-type:jwt-bearer
- client_id: <client id from IAS>
- client_secret: <client secret from IAS>
See screenshot below of sample request and the response from IAS.

Decoding the token, we can see that issuer is set to SAP Cloud Identity Authentication Service tenant. We were able to successfully exchange the token from Azure with one issued by IAS. The attributes you get back in the token will depend upon whether the user record exists in IAS or not. In my case my user also exists in IAS so I see attributes like user_uuid which are available in IAS user profile. If the user record doesn't exist in IAS(pure proxy scenario) the token will be rather basic as shown in my second screenshot below.
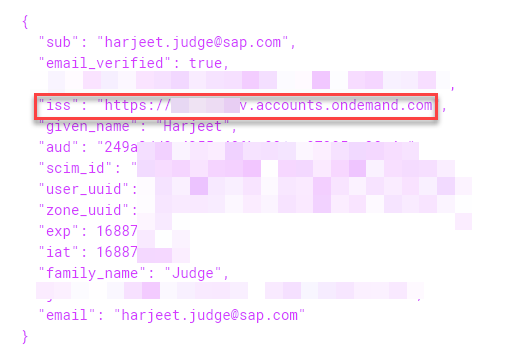
Token if the user doesn't exist in IAS.

As a final step, it's now possible to authenticate to BTP using the token we received from IAS. This is only possible if the BTP subaccount has an OIDC trust setup with IAS. The process will create an application in IAS that should be configured using the steps listed earlier in the blog.

To formulate the authentication request to SAP BTP, we need to perform the following steps:
- Log into BTP Cockpit and create an instance of Authorization and Trust Management Service using the apiaccess plan in your subaccount.

- Click the service to see it's details and click Create to create a new service key.
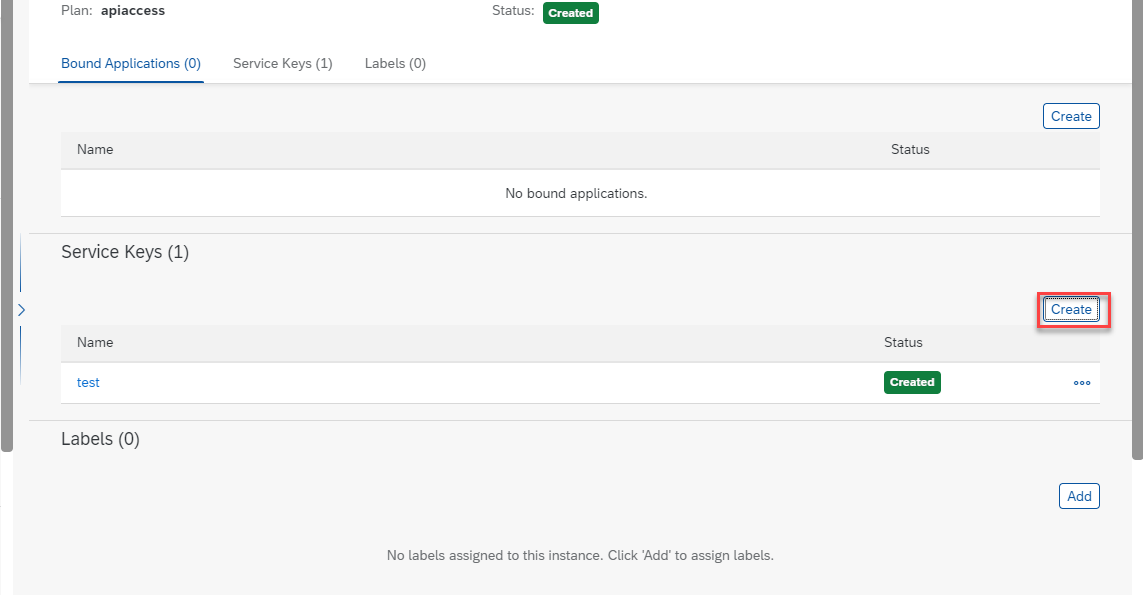
- Provide a name for the key and click create.

- Click on the generated key and make note of the clientid, clientsecret and url fields.

We can now send the request to BTP for authentication. The request should be formulated using the following information:
- Token URL: <url field from key>/oauth2/token
- Request Headers:
- Content-Type: application/x-www-form-urlencoded
- Body:
- assertion: <id token from retrieved from IAS in previous request>
- grant_type: urn:ietf:params:oauth:grant-type:jwt-bearer
- client_id: <client id copied earlier>
- client_secret: <client secret copied earlier>
See screenshot below of sample request and the response from SAP BTP.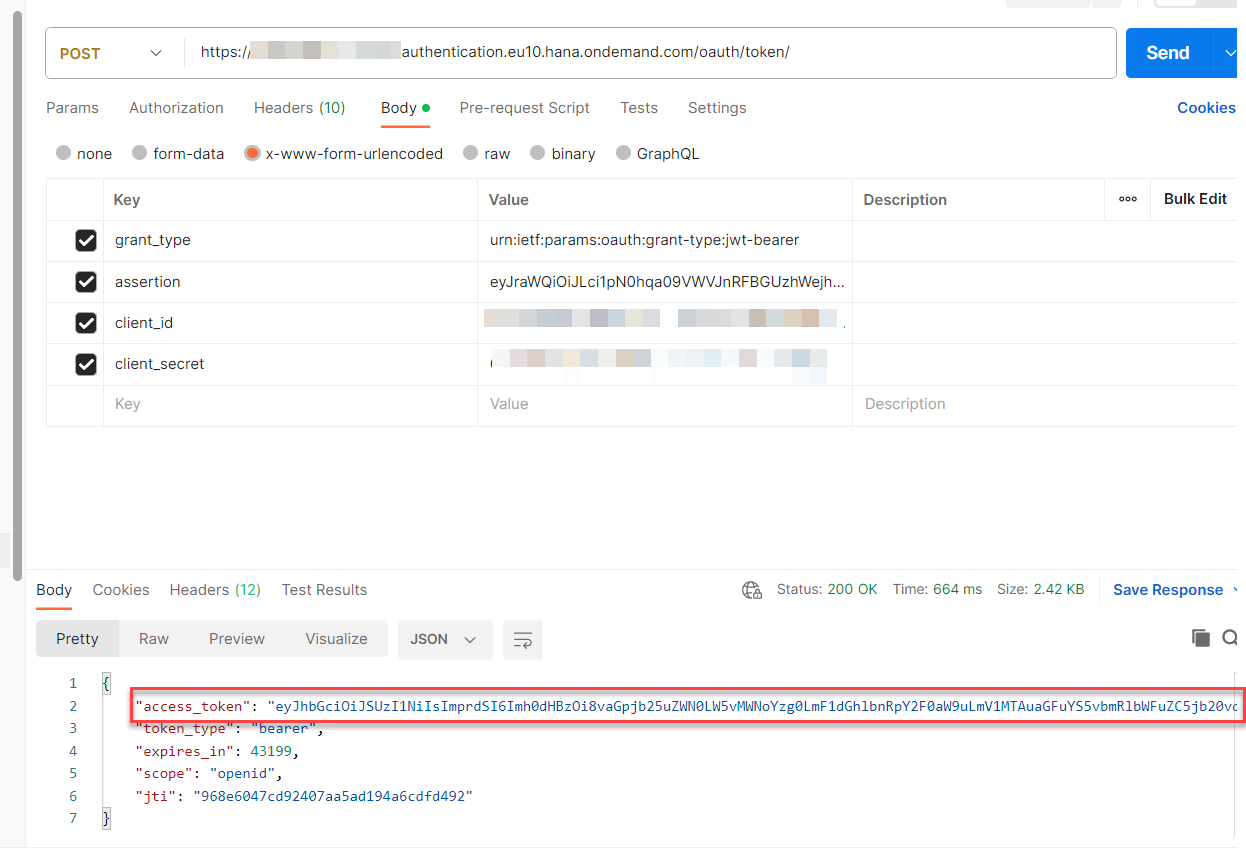
This token can be used to access BTP services within that subaccount. Let's decode the access token to see what information we get back. 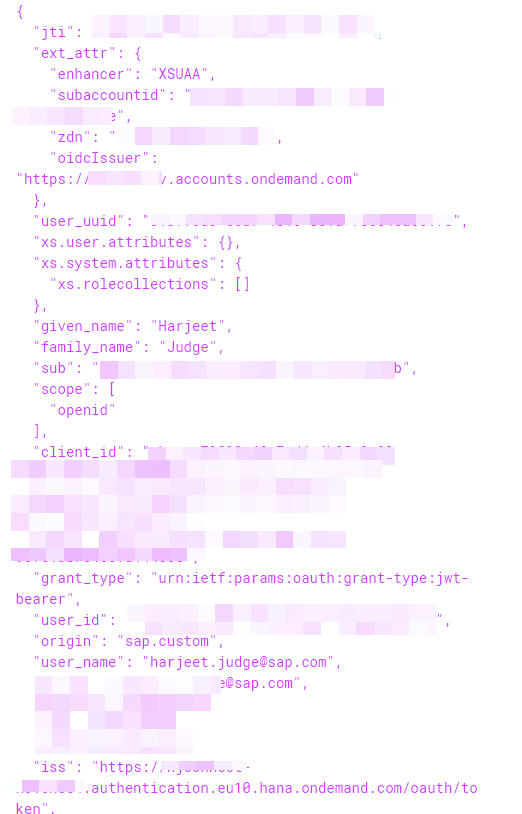
Feedback and comments are welcomed.
- SAP Managed Tags:
- SAP BTP Security,
- SAP Cloud Identity Services
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
103 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
69 -
Expert
1 -
Expert Insights
177 -
Expert Insights
322 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,576 -
Product Updates
368 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
454 -
Workload Fluctuations
1
- Sap Build Andriod app displays black screen after logging in in Technology Q&A
- Consuming SAP with SAP Build Apps - Web App in SAP Build Work Zone, standard edition in Technology Blogs by SAP
- providing IAS authentication through cloud identity service for UI5 MTA app in Technology Q&A
- SAP Cloud ALM and Identity Authentication Service (IAS) in Technology Blogs by SAP
- Configuring SAP CI/CD pipeline for Deploying ReactJS application in Cloud Foundry in Technology Q&A
| User | Count |
|---|---|
| 24 | |
| 8 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 6 | |
| 6 | |
| 6 |