
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Generate JWT Token from CPI
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Employee
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-30-2023
10:55 PM
Generate CDC Bearer Token from JWT hashed with RSA Private Key
REST API requests to SAP Customer Data Cloud should be made securely, the recommended authentication mechanism is to use a bearer token constructed using a unique RSA key. An API request to SAP Customer Data Cloud should be signed using an HTTP bearer token. This replaces the application / user key and secret signature method.
What is JWT?
JSON Web Tokens is an open standard URL-safe way for securely transmitting information between a request & response system. Data in a JWT is encoded as a JSON object. This data is digitally signed using a private key pair using RSA.
JSON Web Tokens consist of three parts separated by a dot,
- Header
- Payload
- Signature
Format of JSON Web Token
[header].[body].[signature]
Header:
{
"alg": "RS256" – JWT Signing algorithm
"typ": "JWT", - JWT
"kid": "<app key>" - User key from the application
}
Body:
{
"iat": 1548189000, - Timestamp that identifies when the JWT was issued
"jti": "b3t567895-r56y-7659-5t6i-t67y64456784",
- A nonce ensuring that this JWT can be used only once
}
Signature:
RSA Private Key converted to PKCS#8 Private Key signed with RSA-256 hashing algorithmLet’s discuss how to generate the JWT bearer token in CPI Groovy Script assuming CPI plays the cloud middleware between the requesting cloud tenant and target Customer Data Cloud.
First step is to upload the RSA Private Key to Keystore in CPI. The RSA private key is provided in SAP Customer Data Cloud console
RSA Private Key copied from CDC Console
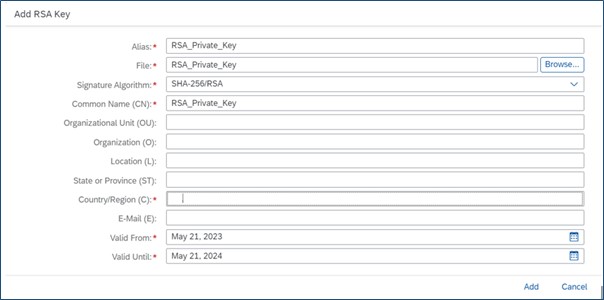
Add RSA Private Key to Security Material
RSA Private Key in Security Material
Now let us create a simple integration flow which will accept a request and return the JWT Bearer Token. Assume the incoming request contains the user key and jti – JWT ID unique for each token request

Integration Flow
Integration flow receives the incoming request and has a content modifier which reads the user key and jti and assigns it to exchange parameters
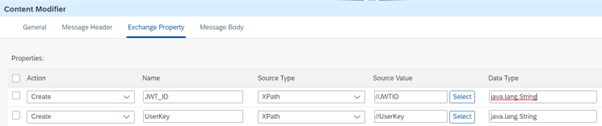
Content Modifier
Next component is the integration flow is the Groovy Script which will read the RSA Private Key from the key store and encoded in base64 format. This will be converted to PKCS8 format and hashed with RSASHA256 algorithm for asymmetric encryption.
Declare the headers,
import com.sap.gateway.ip.core.customdev.util.Message;
import java.util.HashMap;
import io.jsonwebtoken.*
import com.sap.it.api.ITApiFactory;
import java.util.Base64
import java.security.spec.PKCS8EncodedKeySpec
import com.sap.it.api.keystore.KeystoreService;
import java.security.KeyFactory
import java.security.Key;
import java.math.BigDecimal
//Get the timestamp with validity of 1 minute from now
def timeStamp = (System.currentTimeMillis() / 1000 + 60)
timeStamp = timeStamp.setScale(0, BigDecimal.ROUND_DOWN);
//Get the JWT ID and User key from exchange property
jwtid = message.getProperty("JWT_ID")
userKey = message.getProperty("UserKey")
Now formulate the jsonstring with the unique JWT ID and the timestamp generated
String jsonString = """{"iat":${timeStamp}, "jti":"${jwtid}"}""";Read the RSA private key stored in security material
Key privateKey = keyService.getKey("rsa_private_key");
//Encode the key in Base 64
def base64EncodedPrivateKey = (Base64.getEncoder().encode(privateKey.getEncoded()));
Next step is to conver the base 64 encoded RSA private key to Public-Key Cryptography Standards (PKCS)#8
//Create an instance of PKCS8EncodedKeySpec with the given encoded key
def pkcs8KeySpec = new PKCS8EncodedKeySpec(base64EncodedPrivateKey)
//Get an instance of KeyFactory to convert keys to RSA algorithm
def pkcs8KeyFactory = KeyFactory.getInstance("RSA")
//Generate a private key in PKCS8 format
def pkcs8Key = pkcs8KeyFactory.generatePrivate(pkcs8KeySpec)
Call JWTBuilder API to generate a JSON Web Token signed with the PKCS8 private key
String jwtToken = Jwts.builder()
.setHeaderParam("typ","JWT")
.setHeaderParam("alg","RS256")
.setHeaderParam("kid",userKey)
.setPayload(jsonString)
.signWith(SignatureAlgorithm.RS256, pkcs8Key)
.compact();
//Assign the token to message body
message.body = jwtToken
Now, let’s test the integration flow from Postman. Call the integration flow and pass the jti - JWT ID and CDC user key in the payload
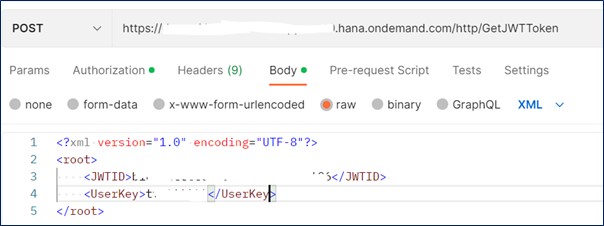
Call Integration Flow from Postman
Integration flow returns the JSON Web Token which can be used to sign requests to Customer Data Cloud

Generated JSON Web Token
The validity time of the JSON Web Token can be increased by changing the timestamp which is currently set to 60 seconds
//Get the timestamp of 1 minute from now
def timeStamp = (System.currentTimeMillis() / 1000 + 60)
timeStamp = timeStamp.setScale(0, BigDecimal.ROUND_DOWN);The jti – unique JWT ID can be generated within groovy script using UUID.randomUUID() method instead of passing it in the call request
jwtid = UUID.randomUUID().toString()Thanks for your time!
Regards,
ArunKumar Balakrishnan- SAP Managed Tags:
- Cloud Integration,
- SAP Customer Data Cloud,
- SAP Customer Data Platform
Labels:
4 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
107 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
72 -
Expert
1 -
Expert Insights
177 -
Expert Insights
340 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
14 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,575 -
Product Updates
384 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,872 -
Technology Updates
472 -
Workload Fluctuations
1
Related Content
- First steps to work with SAP Cloud ALM Deployment scenario for SAP ABAP systems (7.40 or higher) in Technology Blogs by SAP
- Error "Missing JWT Token for forwardAuthToken" When Using worker_threads/spawn in SAP CAP in Technology Q&A
- mongodb - IDT - RIGHT OUTER JOIN in Technology Q&A
- Automated check for SAP HANA Cloud availability with SAP Automation Pilot in Technology Blogs by SAP
- Be a Cockroach: A Simple Guide to AI and SAP Full-Stack Development - Part I in Technology Blogs by Members
Top kudoed authors
| User | Count |
|---|---|
| 17 | |
| 14 | |
| 12 | |
| 10 | |
| 9 | |
| 8 | |
| 7 | |
| 7 | |
| 6 | |
| 6 |