- SAP Community
- Products and Technology
- Human Capital Management
- HCM Blogs by Members
- Efficient Employee Grouping in SAP SuccessFactors:...
Human Capital Management Blogs by Members
Gain valuable knowledge and tips on SAP SuccessFactors HCM suite and human capital management market from member blog posts. Share your insights with a post of your own.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
shrutithakkar
Active Participant
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-21-2023
9:17 PM
Streamlining Employee Grouping in SAP SuccessFactors: Leveraging Custom Attributes from SAP SuccessFactors via Identity Provisioning for Identity Authentication User Store Management.
In this blog, the focus is on streamlining employee grouping in SAP SuccessFactors using custom attributes. For an example we are using custom15 from the User Data file is utilized to determine the appropriate group for employees in the Identity Authentication user store.
There could be different conditions that can be used to check a particular field value and update the employee in a specific group.
The custom attribute (custom15) is utilized as a key factor for grouping employees in SAP SuccessFactors. By checking the value of this field, employees are dynamically assigned to different groups. If the value is set to "Yes", they are directed to the 'MFAGROUP' group in Identity Authentication. On the other hand, if the value is set to anything other than "Yes" (e.g. "No" or left blank), the employees are directed to the 'NO_MFA' group.
By utilizing the "Is MFA?" (Custom15) field, employee grouping in Identity Authentication is streamlined, ensuring that employees are accurately placed in the appropriate groups based on the value of this custom attribute. This approach simplifies user store management and enhances the overall identity and access management process in SAP SuccessFactors.
Step 1- Identity Provisioning Source System - SAP SuccessFactors
The Custom15 value can be added to the sf.user.attributes property in the Identity Provisioning configuration. This allows Identity Provisioning to read and load this user attribute from SAP SuccessFactors during the provisioning process. It is important to ensure that the extra attribute, in this case Custom15, is appropriately separated by a comma to ensure accurate data processing.
Step 2 - Mapping the data in Source System
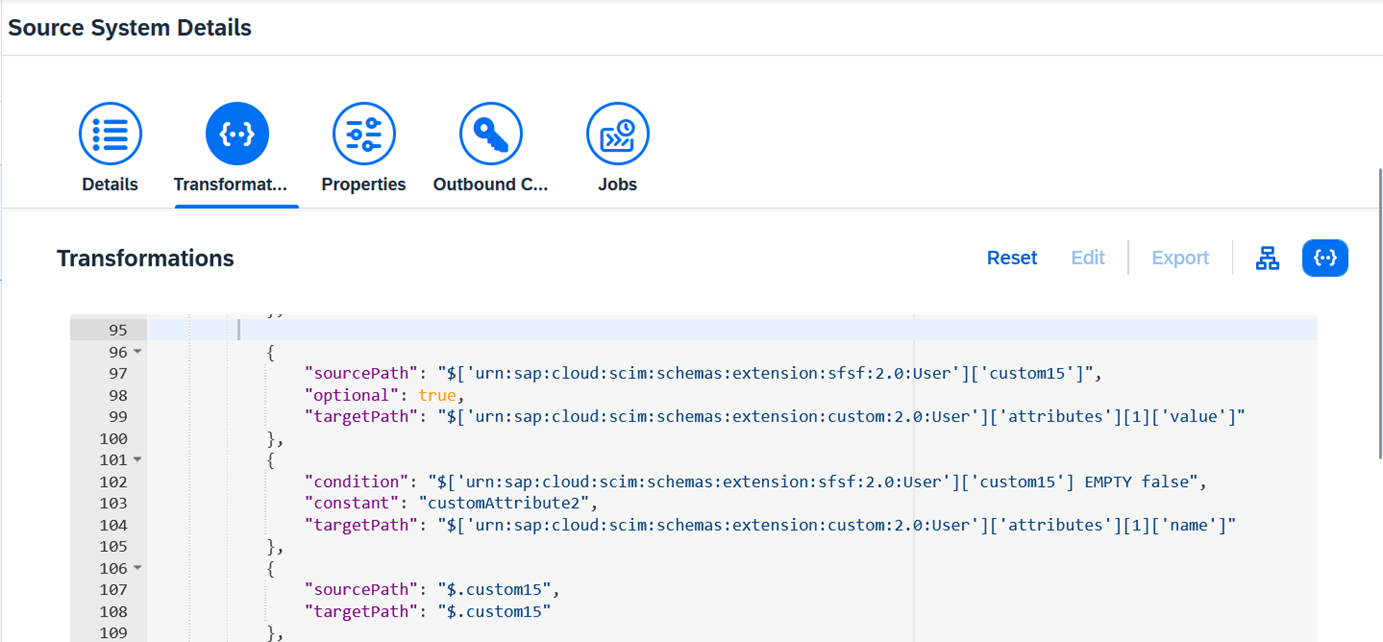
Add the following code to the source system transformation into the User mapping section. I am updating the value of Custom15 from SF into CustomAttribute2 in IAS:
{
Step 3 - Identity Provisioning Target System - Identity Authentication
Add the following code to the Identity Authentication target system transformation into the User mapping Section:
{
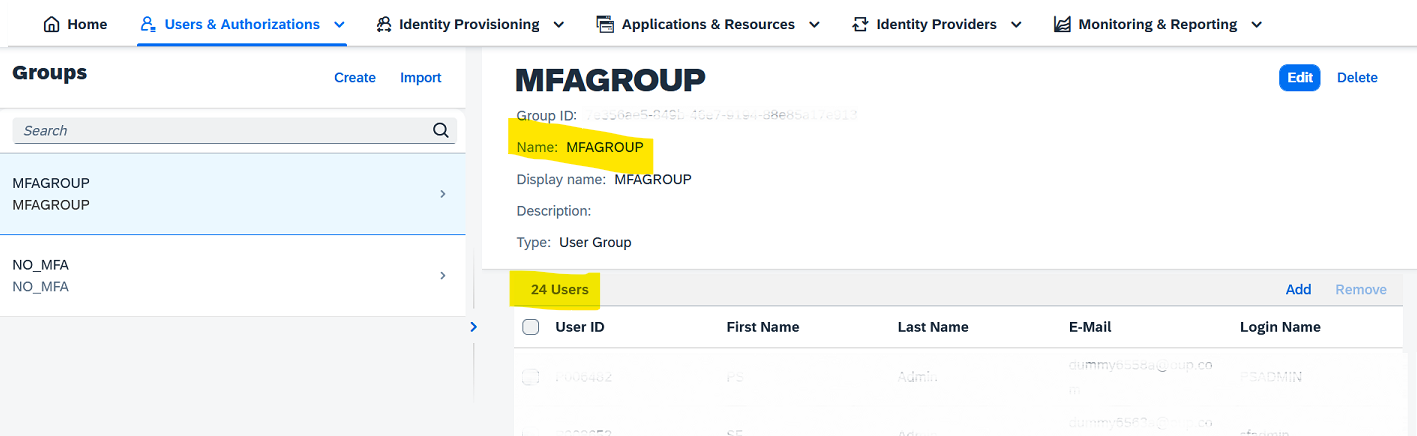
Step 4 - Create the two User Groups
In Identity Authentication Administration Console, create the two user groups to update the employees:
Step 5 - Add Condition for employees to get auto updated in User groups created in Identity Authentication
These mappings will assign the user groups to the users who are fits with the given condition.
{
Step 6- Run Read Job Identity Provisioning
Run a new Read job from Identity Provisioning from SAP SuccessFactors source system, and monitor in Identity Authentication that the employees are getting updated to the desired groups as per the condition we mentioned in step 5.
For Inital Testing, use filter for specific group of employees and once job is successfully; remove the filter and run the job for all active employees.
Finally, remove the employee specific filters and run the job for all active employees. The job should read the value from SF and accordingly update the details in IAS via IPS jobs.
In summary, by using custom attributes from SAP SuccessFactors via Identity Provisioning, employee grouping can be streamlined in SAP SuccessFactors. The steps outlined in this blog provide a straightforward approach to implementing this solution. By mapping the custom attribute field to a target attribute in Identity Authentication, and using conditions to assign employees to specific user groups, the overall identity and access management process in SAP SuccessFactors can be enhanced.
I hope you found this blog post informative and helpful. I would love to hear your thoughts and feedback on this topic, so please feel free to leave a comment below. Feedback, suggestions will help me to continue improving the content and providing with more valuable insights and learn more.
Thank you for reading! Happy Learning!
Thank you 🙂
In this blog, the focus is on streamlining employee grouping in SAP SuccessFactors using custom attributes. For an example we are using custom15 from the User Data file is utilized to determine the appropriate group for employees in the Identity Authentication user store.
There could be different conditions that can be used to check a particular field value and update the employee in a specific group.
The custom attribute (custom15) is utilized as a key factor for grouping employees in SAP SuccessFactors. By checking the value of this field, employees are dynamically assigned to different groups. If the value is set to "Yes", they are directed to the 'MFAGROUP' group in Identity Authentication. On the other hand, if the value is set to anything other than "Yes" (e.g. "No" or left blank), the employees are directed to the 'NO_MFA' group.
By utilizing the "Is MFA?" (Custom15) field, employee grouping in Identity Authentication is streamlined, ensuring that employees are accurately placed in the appropriate groups based on the value of this custom attribute. This approach simplifies user store management and enhances the overall identity and access management process in SAP SuccessFactors.
Step 1- Identity Provisioning Source System - SAP SuccessFactors
The Custom15 value can be added to the sf.user.attributes property in the Identity Provisioning configuration. This allows Identity Provisioning to read and load this user attribute from SAP SuccessFactors during the provisioning process. It is important to ensure that the extra attribute, in this case Custom15, is appropriately separated by a comma to ensure accurate data processing.

sf.user.attributes
Step 2 - Mapping the data in Source System
Add the following code to the source system transformation into the User mapping section. I am updating the value of Custom15 from SF into CustomAttribute2 in IAS:
{
"sourcePath": "$['urn:sap:cloud:scim:schemas:extension:sfsf:2.0:User']['custom15']",
"optional": true,
"targetPath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:User']['attributes'][1]['value']"
},
{
"condition": "$['urn:sap:cloud:scim:schemas:extension:sfsf:2.0:User']['custom15'] EMPTY false",
"constant": "customAttribute2",
"targetPath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:User']['attributes'][1]['name']"
},
{
"sourcePath": "$.custom15",
"targetPath": "$.custom15"
}
Transformation - Source Code - UserMapping
Step 3 - Identity Provisioning Target System - Identity Authentication
Add the following code to the Identity Authentication target system transformation into the User mapping Section:
{
"sourcePath": "$['urn:sap:cloud:scim:schemas:extension:sfsf:2.0:User']['custom15']",
"optional": true,
"targetPath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:User']['attributes'][1]['value']"
},
{
"constant": "customAttribute2",
"targetPath": "$['urn:sap:cloud:scim:schemas:extension:custom:2.0:User']['attributes'][1]['name']"
},

Transformation - Target Code - UserMapping
Step 4 - Create the two User Groups
In Identity Authentication Administration Console, create the two user groups to update the employees:
- MFAGROUP
- NO_MFA

User Groups
Step 5 - Add Condition for employees to get auto updated in User groups created in Identity Authentication
These mappings will assign the user groups to the users who are fits with the given condition.
{
"condition": "($.custom15 == 'Yes')",
"constant": "MFAGROUP",
"targetPath": "$.groups[0].value"
},
{
"condition": "($.custom15 != 'Yes')",
"constant": "NO_MFA",
"targetPath": "$.groups[0].value"
},

Transformation - Target Code - UserMapping - Groupingcode
Step 6- Run Read Job Identity Provisioning
Run a new Read job from Identity Provisioning from SAP SuccessFactors source system, and monitor in Identity Authentication that the employees are getting updated to the desired groups as per the condition we mentioned in step 5.
For Inital Testing, use filter for specific group of employees and once job is successfully; remove the filter and run the job for all active employees.

Custom Attribute 2 = Yes
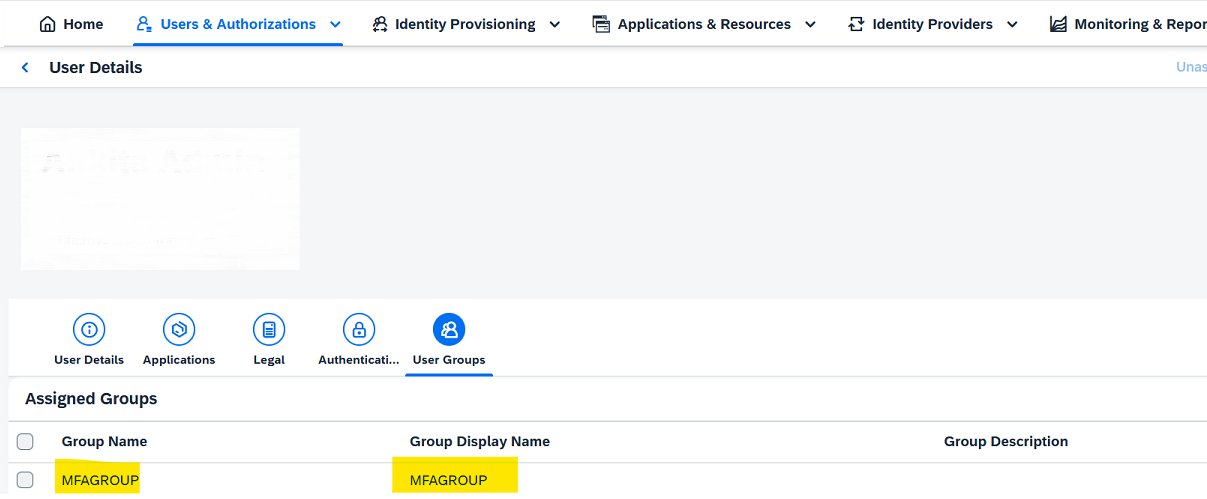
User Group updated in User Profile
Finally, remove the employee specific filters and run the job for all active employees. The job should read the value from SF and accordingly update the details in IAS via IPS jobs.
Group 1, Custom Attribute == Yes

Group 2, Custom Attribute != Yes
In summary, by using custom attributes from SAP SuccessFactors via Identity Provisioning, employee grouping can be streamlined in SAP SuccessFactors. The steps outlined in this blog provide a straightforward approach to implementing this solution. By mapping the custom attribute field to a target attribute in Identity Authentication, and using conditions to assign employees to specific user groups, the overall identity and access management process in SAP SuccessFactors can be enhanced.
I hope you found this blog post informative and helpful. I would love to hear your thoughts and feedback on this topic, so please feel free to leave a comment below. Feedback, suggestions will help me to continue improving the content and providing with more valuable insights and learn more.
Thank you for reading! Happy Learning!
Thank you 🙂
12 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
1H 2024 Product Release
5 -
2H 2023 Product Release
1 -
Absences-Only Time Recording in SAP SuccessFactors
1 -
ACCRUAL TRANSFER
1 -
Advanced Workflow
1 -
AI
1 -
AI & Skills Ontology
1 -
Alerts for National ID Information portlet: Full step-by-step guide
1 -
Alerts for Payment Information: Full step-by-step guide
1 -
Anonymization
1 -
API and Integration
1 -
Auto Delegation on the Leave Request (Time Off) Screen
1 -
BTP
1 -
Business Rules
2 -
Calibrating with Performance Form Data
1 -
Canvas Report
1 -
Career Development
1 -
Certificate-Based Authentication
1 -
Cloud Identity Services
1 -
Cloud Platform Integration
1 -
Common Super Domain
1 -
Compensation
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
2 -
Content
1 -
Conversational AI
2 -
CSD
1 -
Custom Data Collection
1 -
Custom event
1 -
custom portlet
1 -
Data & Analytics
1 -
Data Integration
1 -
Dayforce
1 -
deep link
1 -
deeplink
1 -
Delimiting Pay Components
1 -
Deprecation
1 -
EC Payroll
1 -
Employee Central
1 -
Employee Central Global Benefits
1 -
Employee Central Integration (Inc. EC APIs)
1 -
Employee Central Payroll
2 -
employee profile
2 -
Employee Rehires
2 -
external terminal
1 -
external time events
1 -
Generative AI
2 -
Getting Started
1 -
Global Benefits
1 -
Goals
1 -
Guidelines
1 -
h12024
1 -
H2 2023
1 -
HCM
1 -
HR
2 -
HR Data Management
1 -
HR Transformation
1 -
ilx
1 -
Incentive Management Setup (Configuration)
1 -
Integration Center
3 -
Integration Monitoring
1 -
Integration Suite
1 -
Intelligent Services
1 -
internal mobility
1 -
Introduction
1 -
Learning
3 -
LMS
2 -
LXP
1 -
Managing Pay Scale Progression based on Age (or) Service Period
1 -
Massively MDF attachments download
1 -
Mentoring
1 -
Metadata Framework
1 -
Middleware Solutions
1 -
OCN
1 -
ODATA
1 -
OData APIs
2 -
ONB USA Compliance
1 -
Onboarding
2 -
Opportunity Marketplace
1 -
Pay Component Management
1 -
PCE
1 -
Performance & Goals
1 -
Performance Form
1 -
Performance Forms
1 -
Platform
1 -
portlet
1 -
POSTMAN
1 -
Predictive AI
2 -
Recruiting
1 -
recurring payments
1 -
RISE PCE
1 -
Role Based Permissions (RBP)
2 -
S4 HANA On-Premise
1 -
SAP Build CodeJam
1 -
SAP Build Marketplace
1 -
SAP CPI (Cloud Platform Integration)
1 -
SAP HCM
1 -
SAP HCM (Human Capital Management)
3 -
SAP HCM ECC
1 -
SAP HR Solutions
2 -
SAP Integrations
1 -
SAP release
1 -
SAP successfactors
6 -
SAP SuccessFactors OData API
2 -
SAP Workzone
1 -
SAP-PAYROLL
1 -
self-service migration
1 -
sftp
1 -
SFTP scenario
1 -
Skills
1 -
Skills Management
1 -
sso deeplink
1 -
Stories in People Analytics
3 -
Story Report
1 -
SuccessFactors
3 -
SuccessFactors Employee central home page customization.
1 -
SuccessFactors Onboarding
1 -
successfactors onboarding i9
1 -
SuccessFactors Platform
1 -
Table Report
1 -
talent
1 -
Talent Intelligence Hub
2 -
talentintelligencehub
1 -
talents
1 -
Tax
1 -
Tax Integration
1 -
TIH
1 -
Time Accounts
1 -
Time Management implementation links
1 -
Workflows
1 -
XML Rules
1
- « Previous
- Next »
Related Content
- SuccessFactors LMS - Adding Module and Item to overdue Program in Human Capital Management Q&A
- SuccessFactors HCM 1H 2024 Release Highlights / Reporting in Human Capital Management Q&A
- Reporting on all Performance Form Scores in Human Capital Management Q&A
- FC Bayern elevates their HR strategy with SAP SuccessFactors and AI-enabled recruiting in Human Capital Management Blogs by SAP
- SuccessFactors EC fields permission in Human Capital Management Q&A
Top kudoed authors
| User | Count |
|---|---|
| 5 | |
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 |