- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- Consuming SAP with SAP Build Apps - Connectivity o...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This blog post is the second in a series of posts that cover the connectivity options available for SAP Build Apps to interface with SAP systems. In case you've missed it, part 1 of the series can be found here. The series will cover connecting SAP Build Apps with the following:
- CAP-based services
- S/4HANA systems
- ABAP systems
The format of this post is similar to a tutorial. However, I'll provide more comprehensive details, tips and the opportunity for you to provide feedback. Based on the feedback we will be able to adjust and enhance this post and future parts of the series, and might even be able to improve the products involved as well. Just like in real-world scenarios, we will start with a very basic app and gradually enhance it.
Introduction
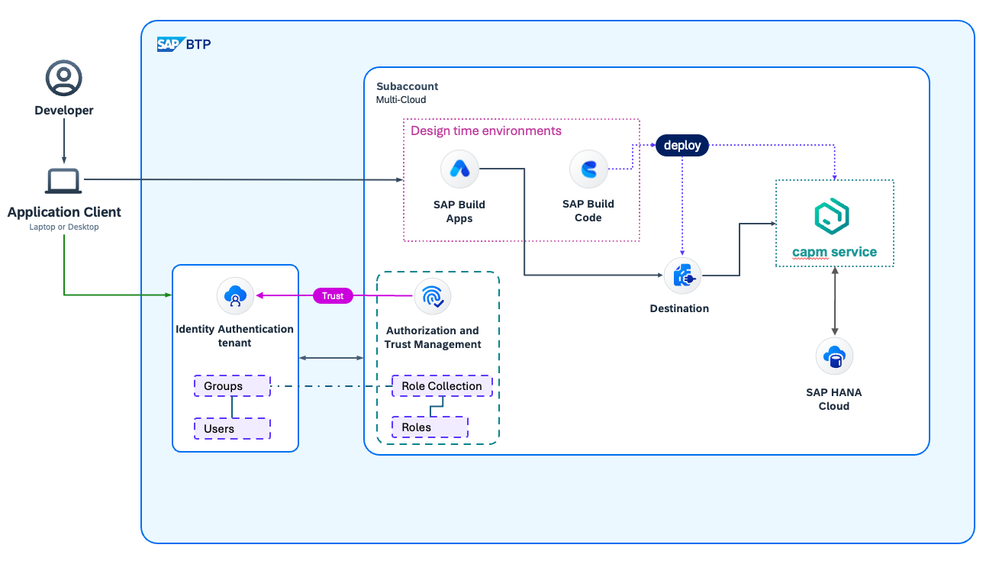
Before we get into the details of setting up connections between SAP Build Apps and SAP Systems, I intend to introduce SAP technology components in each post that are relevant for the use cases covered in the series.
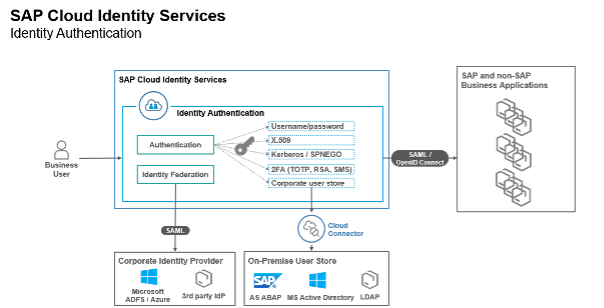
IAS
SAP Identity Authentication Service (IAS) is a cloud service for authentication, single sign-on, and user management in SAP cloud and on-premise applications. It can act as an identity provider or be used as a proxy to integrate with an existing single sign-on infrastructure. IAS offers the following features:
- Authentication: Standardized methods, flexible options, and password policies
- Integration: Flexible scenarios with existing identity providers and corporate IdPs
- User experience: Customizable look-and-feel, self-service capabilities, and invitation workflows
- Security: Risk-based authentication, two-factor authentication, and delegated authentication
Use case B : Control access to the CAP service through Roles
For this use case, we will enhance the previously created basic CAP project in SAP Build Code and introduce Roles to control access to the service. Depending on the user’s Role, the access and capabilities are controlled. As SAP Build Apps uses IAS for authentication, the configuration is a bit more complicated. Follow along the steps below to learn how to get this set up.
Creating Roles
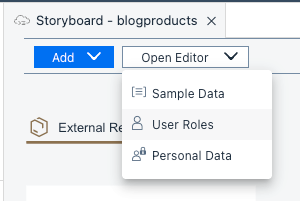
We go back to the Storyboard in SAP Build Code (or SAP Business Application Studio, depending on your subscription) and select the menu Open Editor. Select User Roles. This will open the Authorization Editor.
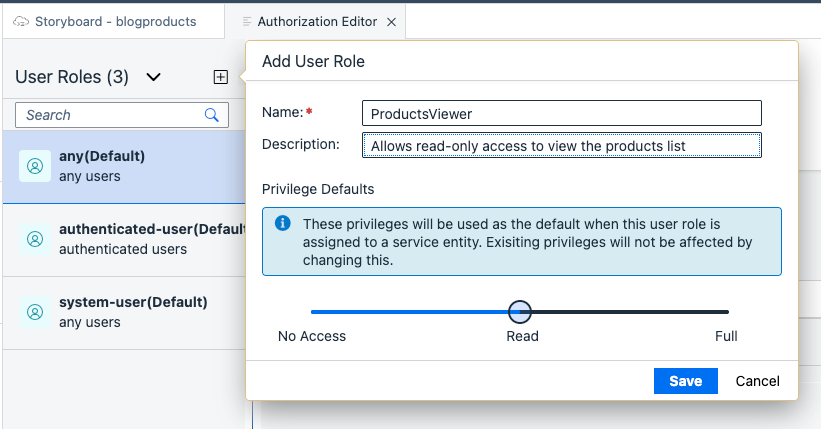
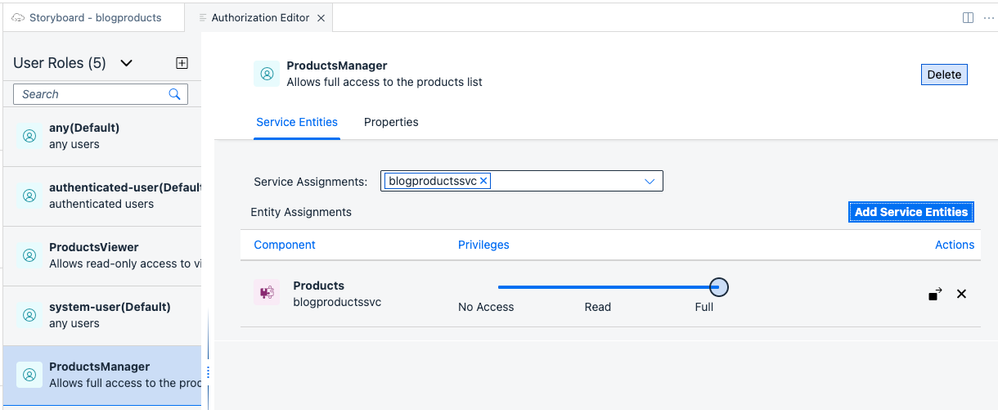
First, let’s create a role called ProductsViewer, allowing the user to read the product list. Select the + button to add a new role, configure as shown below and save it.
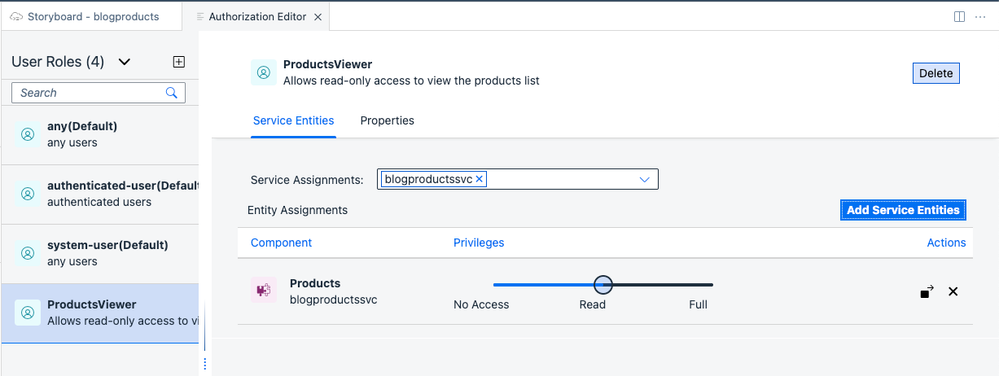
Select the ProductsViewer role and select your service for the Service Assignments. Click Add Service Entities and toggle the Assigned button for Component "Products" to On. For the Privileges, keep the default "Read". Select Save. The ProductsViewer should now be configured as follows:
We will add another role called ProductsManager, allowing full access to the data. We could go even further into details on which actions a user is allowed to perform (e.g. Read, Update, Delete). But to keep this example short, we’ll just give the manager full access.
To apply this Role-based access control to the service, we will have to redeploy it. Follow the steps as mentioned previously to deploy the CAP-based service.
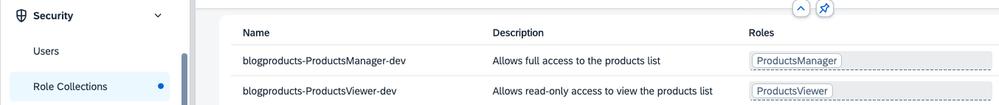
After successful redeployment, you will find 2 new Role Collections in your BTP subaccount's cockpit. The names of the Role Collections were automatically generated and contain the roles we had specified in the Authorization Editor.
Informing the user in case data access is denied
Before we move on and run the UI application, let's add a small enhancement in SAP Build Apps to inform the user when data access is denied. Without this enhancement the user will be left in the dark in case the products list is not showing up.
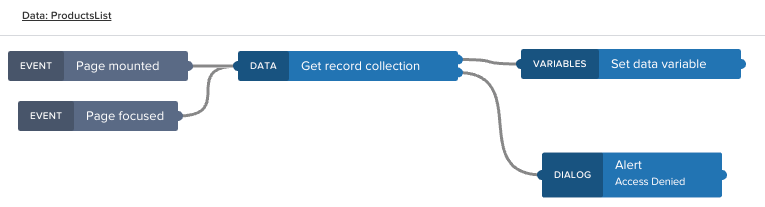
Go to the SAP Build Apps designer and select the UI CANVAS tab. Switch from VIEW to VARIABLES. Go to DATA VARIABLES and select the ProductsList we have added in the previous blog post. At the bottom of the page, open the logic canvas by selecting the "Add logic to HOME PAGE". Now drag and drop "Dialog | Alert" onto the canvas. Connect the failure output node (bottom connector) of "Data | Get record collection" to the input node of "Dialog | Alert".
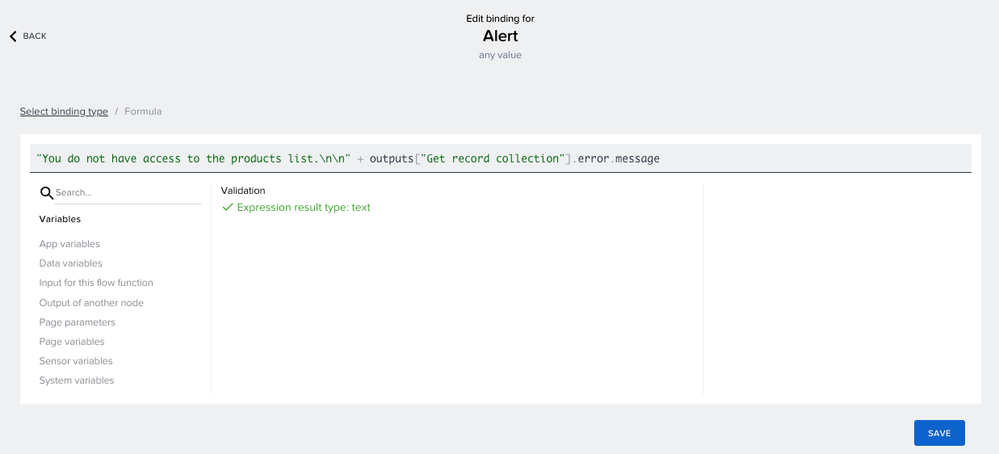
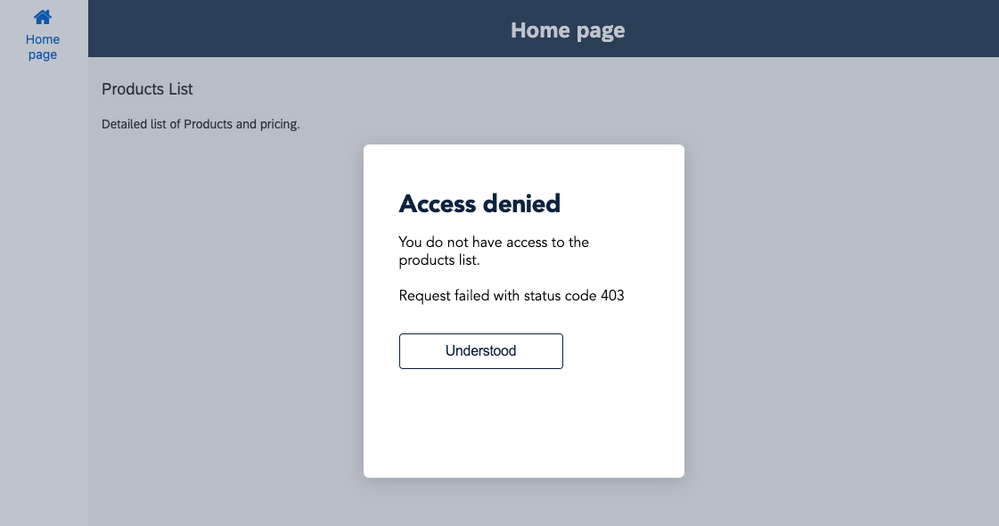
Select the alert dialog and change the title. For this example use case, I am going to make the assumption that in case of any failure, the reason is that the user doesn't have access to the service data. There could actually be other reasons, but we'll ignore this here. Change the Dialog title to "Access denied". For the Dismiss button label, you can use the default "Ok". In my case, I've changed it to "Understood". For the dialog message, bind a formula as shown below and save your changes. Besides the message "You do not have access to the products list.", the formula will output the technical error message.
Quick preview of the UI app
We are actually not done configuring the Role Collections for your user at this point. So let us try the enhancement. If we would run the app now, it should inform us that access is denied.
In SAP Build Apps, select the LAUNCH tab and select "Open preview portal".
Assigning Roles to users
To provide the user access to the data service, we now have to ensure the user has the required Roles assigned. For this, we have 2 options:
- Assign Role Collections to the Custom IdP (IAS) user in the BTP Cockpit.
- Create a Group in the custom IdP; assign users to this group; and map this Group to a Role Collection in the BTP Cockpit. This is a better option in case you are planning to expose the data to a larger group of users.
Assign Role Collection to the Custom IdP user in the BTP Cockpit
Assigning the role collection to the custom IdP user works best for the developer use case, where a limited set of users is to be provided access to the data offered through the service. You'll basically have to apply this for each user / developer in your team.
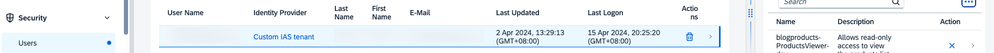
Go to the BTP subaccount cockpit and navigate to the Security > User tab. As you are using two identity providers, you will see your user for the Identity Provider “Custom IAS tenant” and “Default identity provider”. SAP Build Apps makes use of the “Custom IAS tenant”. Therefore, we need to ensure this user is assigned to the necessary Role Collection. Depending on your use case, you can assign yourself the “manager” or “viewer” role, as defined for your service.
Note that without assigning a Role Collection to your user, you will not have access to the data. You will still be able to connect to the destination and check the entity types exposed; but you will not see any data and receive a 403 error, indicating you have no permission to access the data itself. In case you run into this, and you've updated the Role Collections assigned to your user, then please log out and log in again to ensure the new Roles take effect.
Mapping a Group in Custom IAS tenant to a Role Collection in the BTP Cockpit
As mentioned, this option is more suitable when managing access for larger group of users.
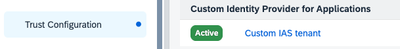
Go to the BTP subaccount cockpit and navigate to the Security > Trust Configuration tab. Open the link to the Custom IAS tenant.
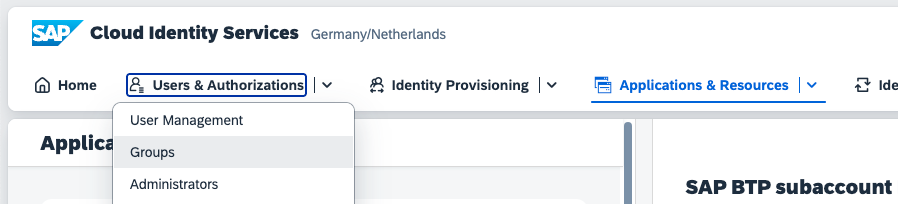
On the overview page, open the link to the Host Name of Identity Authentication Tenant. This brings you to the administration page of the SAP Cloud Identity Service. Assuming you have set up a user here, navigate to Users & Authorizations > Groups.
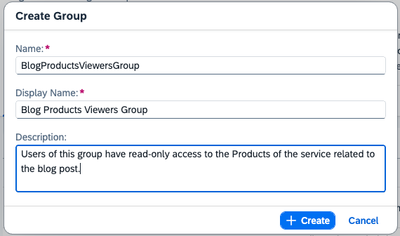
Select the “+ Create” button to create a new Group. Provide a Name, Display Name and description.
Once the group is created, select it to manage the users of the group. Select the “+ Add” button. You can easily pick users known in the system.
Follow the same steps to create a new Group for Managers who have full access.
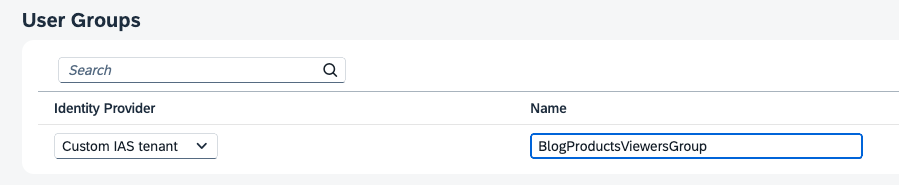
Now that you’ve set up Groups in SAP Cloud Identity Services, go back to the BTP subaccount cockpit and navigate to the tab Security > Role Collections. Select the Role Collection you want to assign to the IAS Group. Select the “Edit” button, so you can make changes. In the section User Groups, you can select the Identity Provider “Custom IAS tenant” and enter the exact name of the Group, as defined in IAS.
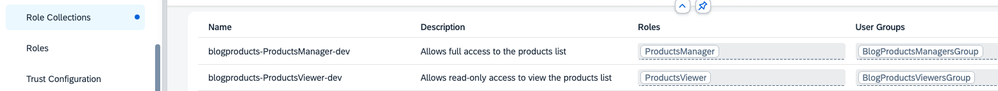
Save your changes. The mapping will also be reflected in the Role Collections overview.
Testing the newly added access control
To test the access control, please assign only the 'Viewer' Role Collection to your user. Take note that there are two ways to do this: in SAP Cloud Identity Services and in the BTP subaccount cockpit.
Log out and log in again to ensure your changes are used in the system. Please note that changes in Role Collections assigned to custom IdP users can take some time to propagate. If you notice your changes have not taken effect yet, please have some patience.
The app we have created so far only allows users to view a product list. To make changes or add new entries, we can use the data functionality built into SAP Build Apps. Open SAP Build Apps, navigate to the Data tab and select the Products OData integration. Select BROWSE REAL DATA.
If you don't see data for the Products entity, then you've probably missed a step described above.
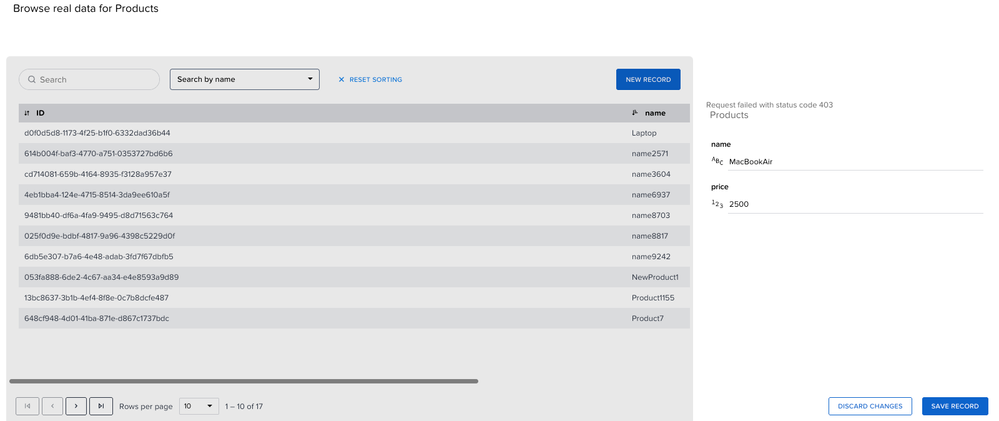
Select an entry and make changes to the name and the price. Then, select SAVE RECORD.
Having the Viewer role, you will not be able to change or add entries. Your request will fail with status code 403.
When you add the Administrator role collection to your user, you will be able to change and add records. But again, please note that you'll have to log out and log in again, and have some patience before these changes take effect.
Note that we have not (yet) deployed any UI application at this point. We have been running our app in the context of SAP Build Apps.
Summary – use case B
Without writing a single line of code, we have added Role-based access control to the CAP-based service. With this in place, authentication to the platform is not enough for users to access the data we have exposed through the service. We have added Roles to the user by assigning platform Role Collections to the Custom IdP user or mapping the Custom IdP group to a specific Role Collection. Depending on platform Roles assigned, a user will be able to perform specific actions on the data. The service is still made available to platform users through a BTP destination and it is discoverable for SAP Build Apps. In SAP Build Apps, we have added an integration to the CAP service through the destination. The destination forms the bridge between the CAP-based service and the applications consuming it.
What's next
In the next blog post, we will create dedicated mobile apps that can consume the data service we have enhanced in this post. For authentication, we will be adding SAP Mobile Services into the solution diagram.
- SAP Managed Tags:
- SAP Business Application Studio,
- SAP Build Apps,
- SAP Build Code,
- SAP Build
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
94 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
67 -
Expert
1 -
Expert Insights
177 -
Expert Insights
306 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
13 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,576 -
Product Updates
349 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,873 -
Technology Updates
434 -
Workload Fluctuations
1
- SAP Datasphere + SAP S/4HANA: Your Guide to Seamless Data Integration in Technology Blogs by SAP
- Get started with SAP BTP ABAP Environment: Trial Account vs. Free Tier Option in Technology Blogs by SAP
- Extract blob data (PDF) from CAPM using python library of Document information extraction service. in Technology Blogs by Members
- Consuming SAP with SAP Build Apps - Mobile Apps for iOS and Android in Technology Blogs by SAP
- Improving Time Management in SAP S/4HANA Cloud: A GenAI Solution in Technology Blogs by SAP
| User | Count |
|---|---|
| 23 | |
| 19 | |
| 12 | |
| 10 | |
| 10 | |
| 9 | |
| 9 | |
| 8 | |
| 7 | |
| 7 |