
- SAP Community
- Products and Technology
- Technology
- Technology Blogs by SAP
- De-mystifying SAP Cloud Identity Services Integrat...
Technology Blogs by SAP
Learn how to extend and personalize SAP applications. Follow the SAP technology blog for insights into SAP BTP, ABAP, SAP Analytics Cloud, SAP HANA, and more.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Product and Topic Expert
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-02-2023
5:15 PM
Motivation & Goal
The setup described in this blog focuses on SAP Build Work Zone, advanced edition & SAP SuccessFactors Work Zone, though a subset of the steps also applies to SAP Build Work Zone, standard edition (basically excluding the ‘DWS’ aspect – see below).
We will explain the different trust setups with SAP Cloud Identity Services you typically encounter when setting up SAP Build Work Zone or SAP SuccessFactors Work Zone.
The new direct integration (explained in context of this blog) is also the pre-requisite for using some of the new features across SAP Build Work Zone already. For now, this applies to the full usage of the custom domain feature which requires the direct integration to also work with integrated business content. Furthermore, this direct integration enables the usage of a custom domain when going beyond the standard edition of SAP Build Work Zone.
Please also note that same direct integration with SAP Cloud Identity Services is also applicable to SAP Build Apps, though the screenshots & description below focus specifically on Work Zone.
Different Types of Trust Setup
For this example, a fresh global account with one subaccount including subscription to SAP Build Work Zone, advanced edition, was created. As a result, there are 4 trusted applications created in SAP Cloud Identity Services (Identity Authentication, IAS) automatically or manually.
In general, 2 scenarios need to be distinguished from an SAP BTP trust setup perspective which we will explore in more detail:
- Platform login to manage global account, subaccount, and environments (using BTP cockpit or btp CLI)
- Application login (either using a shared trust for all services running in the subaccount and/or a direct integration with a respective service)
While an end user of a given application – like SAP Build Work Zone – will mostly only login to the application itself (using the application login), a system administrator will typically utilize both aspects. The administration console of Work Zone for example is part of the regular application (hence using the application login), whereas access to more platform-level topics like SAP BTP destinations is handled via the platform login.
Platform Login
This platform-level trust is used when accessing the SAP BTP global account directory, subaccounts & environments. In this context, access can either happen via the SAP BTP cockpit or the btp CLI (command line interface).
While login to the SAP BTP Multi-Cloud environment cockpit is possible via SAP ID Service (or SAP Universal ID), we recommend using your own IAS tenant – either as the primary identity provider (IdP) and/or as a proxy towards an existing corporate IdP / setup.
This is an automated, well-documented setup process that can be triggered using the ‘Establish Trust’ button on the SAP BTP global account cockpit > Security > Trust Configuration screen:

It will automatically create an application called ‘SAP Business Technology Platform’ in the selected IAS tenant. This setup is only offered based on the OpenID Connect (OIDC) protocol.

While the platform-level trust setup is done on the global account level, it automatically applies to all global accounts which you connect to the tenant, all contained multi-environment and Neo subaccounts, and the Cloud Foundry environment as well:

See here for more details: https://help.sap.com/docs/btp/sap-business-technology-platform/trust-and-federation-with-identity-pr...
Application login – shared trust
In addition to the platform login, there is also the dedicated authentication flow for the services & subscriptions available on the subaccount. Also here, the default trust is still with SAP ID Service, but many SAP BTP products including SAP Build Work Zone or SAP Build Apps already require an integration with IAS as part of the initial product setup.
While the IAS trust setup can be configured manually (based on SAML2.0 protocol), the recommended configuration is to leverage the automated trust setup feature (see below). The setup will automatically create a dedicated application in IAS specific to this subaccount; based on the OpenID Connect (OIDC) protocol. This trust is then used for all services & subscriptions in the respective subaccount. For instance, SAP Build Process Automation, SAP Build Apps, SAP Business Application Studio or SAP Build Work Zone (all editions).
Using the ‘establish trust’ button on the SAP BTP subaccount cockpit > Security > Trust Configuration screen the trust setup can be triggered:
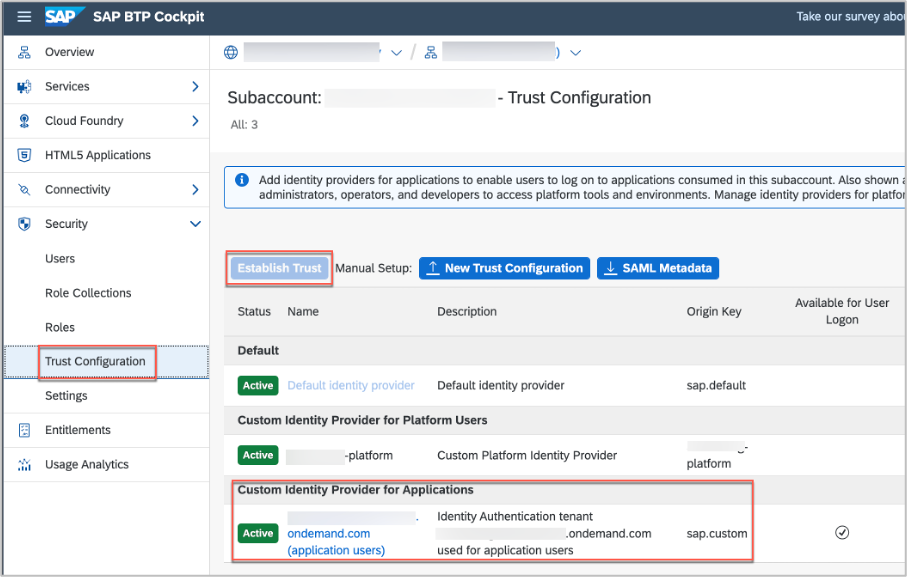
Note: If you are already using the SAML-based trust configuration, please refer to the following guide to learn how to safely migrate to the required OIDC trust. In cases of using other services (which don't yet require IAS) your existing trust configuration could even be with your corporate identity provider (IdP) and not your IAS tenant; this scenario is also covered [to move to IAS instead]: https://help.sap.com/docs/btp/sap-business-technology-platform/migration-from-saml-trust-to-openid-c...
You will then find an automatically created 2nd application in IAS with the name ‘XSUAA_<subaccount name>’:
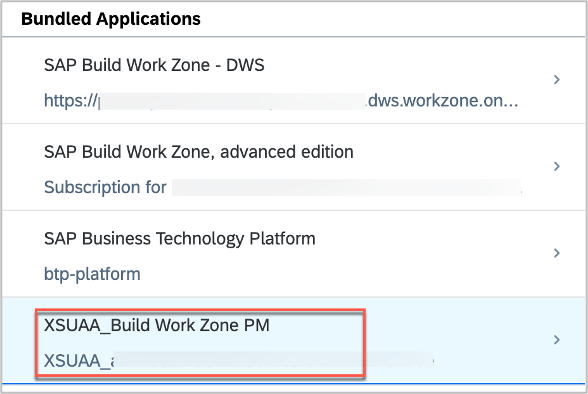
See here for more details: https://help.sap.com/docs/btp/sap-business-technology-platform/trust-and-federation-with-identity-pr...
Application login – direct integration
Until the Q1 2023 release of SAP Build Work Zone, the shared trust (either manual or automated) was utilized for the authentication flow. This setup, however, did not allow for features like custom domain to be used with support for integrated business content.
We now offer a new feature called direct integration of Work Zone with IAS, again based on the OIDC protocol. You will find this as the 3rd application in IAS referring to the respective name of the product, for instance ‘SAP Build Work Zone, advanced edition’.

Depending on the product edition, the description / title of the application will automatically reflect the correct name accordingly (but you can adjust it if required). In the example above, the setup was done for ‘SAP Build Work Zone, advanced edition’.
While the subaccount-level trust is no longer utilized for the login to Work Zone itself once this direct integration with IAS is set up, the shared trust setup on the subaccount level is still required for Work Zone as well as other services. Do not delete the subaccount level trust!
For SAP Build Work Zone, advanced edition & SAP SuccessFactors Work Zone there is a 4th trust setup / application created which will be covered in this blog. For now, all steps described are equally applicable to all product editions of Work Zone (including standard edition).
How to setup direct integration of Work Zone with IAS
Basic Setup
While the setup of the SAP BTP platform-level trust (for the SAP BTP cockpit or btp CLI) is recommended, it is not technically required for utilizing the direct IAS integration of applications like SAP Build Work Zone. You will however need to have the OIDC-based trust on the subaccount-level already using the ‘establish trust’ feature. This now also works when using a custom domain for your IAS tenant. The subaccount-level trust controls which IAS tenant with which domain is used by applications in the subaccount.
Note: If you have other active trusted IdPs configured on the subaccount level, please make sure to temporarily disable them (active = false) for the initial setup as highlighted in the SAP Build Work Zone product setup documentation.
With the pre-requisites in place, the direct integration with IAS can easily be configured by an administrator as a self-service in the design time (DT) UI from the > Site Manager > Settings > Identity Authentication screen of Work Zone:
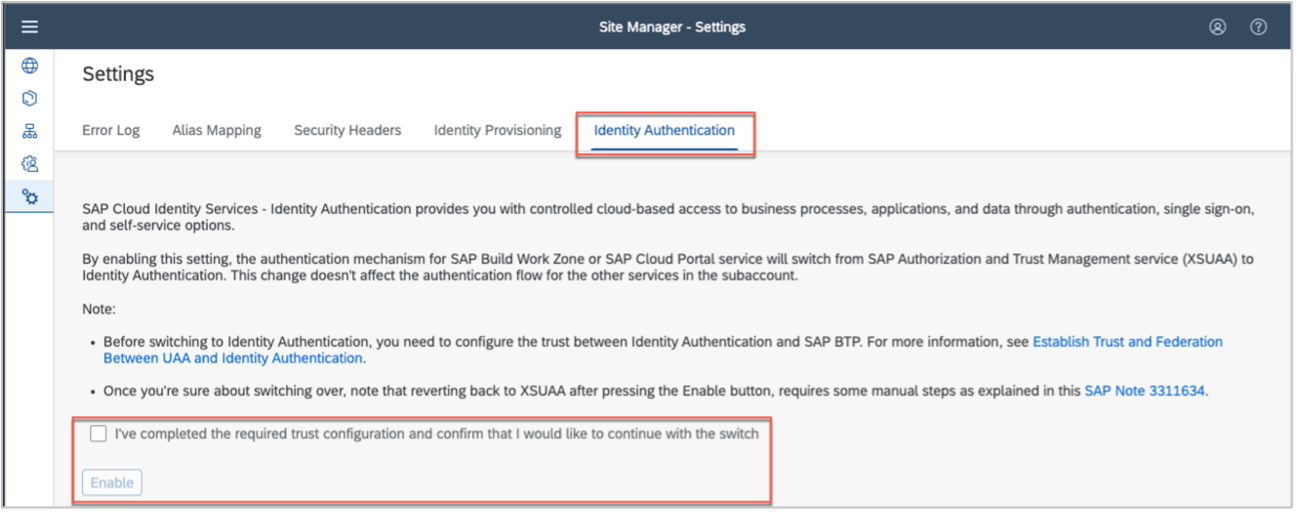
One the setup has completed successfully, this screen will reflect this as follows:
 … and the dedicated application in IAS will be created (see above).
… and the dedicated application in IAS will be created (see above).Configuration Considerations
Once activated, the previously configured trust configuration on subaccount level will no longer apply to Work Zone. Hence, the IAS-level settings such as subject name identifier, conditional authentication setup for corporate IdPs, branding, risk-based authentication rules, assertion attributes & more will need to be (re-)applied to the Work Zone-specific application accordingly.
Further to the IAS-level changes, please also note that SAP BTP configurations such as the userIdSource property in destinations leveraged in Work Zone will now refer to the direct IAS integration setup for Work Zone, no longer the shared trust.
Role of subaccount-level users & role collections for SAP Build Work Zone
At the same time, SAP Build Work Zone still utilizes the subaccount-level (shadow) users as well as role (collections) assigned to those users. Even with the direct IAS integration setup in place, the guidance for managing those users & role collection mappings remains the same.
Users can either be created manually on the BTP cockpit, automatically based on the login via the connected IAS tenant or programmatically using the SAP Authorization and Trust Management Service (XSUAA) API.
Similarly, role collections can be assigned to those users via one of the following ways:
- Manual assignment done in the SAP BTP cockpit. For more information, see Assigning Role Collections
- Using assertion attribute mapping (e.g. “Groups”), as documented in the Onboarding to SAP Build Work Zone, advanced edition
- Using an API-based assignment of users (e.g. via an Identity Provisioning target system). For more information, see Access Administration Using APIs of the SAP Authorization and Trust Management Service
Role of Digital Workplace Service (DWS) trust
The items covered thus far are also fully applicable to SAP Build Work Zone, standard edition. There is however a 4th trust only applicable to SAP Build Work Zone, advanced edition & SAP SuccessFactors Work Zone. The trust setup for this SAML-based application referring to the Digital Workplace Service (DWS) component is done manually by exporting / importing the SAML2.0 metadata shown in the setup configurator. Hence there is also no default naming pattern for this application:

In contrast to either of the application login setups covered thus far, the authentication for the Digital Workplace Service (DWS) iframe component is achieved through a single_use_token, generated via an API call using the 'JAM' destination using OAuth2SAMLBearerAssertion as the authentication mechanism.
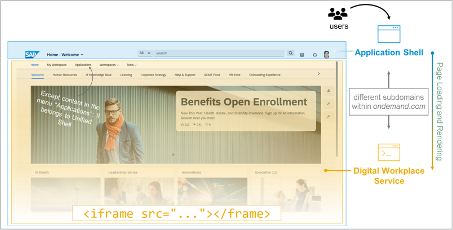
This process is transparent to the users of SAP Build Work Zone, advanced edition, or SAP SuccessFactors Work Zone, and doesn't require any additional login screen or other form of user interaction. In case the API call to create this single use token fails for some reason, the Digital Workplace Service (DWS) <> Identity Authentication (IAS) trust based on SAML2.0 is leveraged as a fallback solution.
Given that this scenario and implied configuration of all involved components is not the primary subject of this blog, please refer to the following section of our learning journey for more details.
What’s Next
In addition to the immediate benefit of being able to utilize a custom domain across all editions of SAP Build Work Zone and the added flexibility of configuring the Work Zone application trust separately from other services on SAP BTP, this direct integration with IAS will enable further exciting scenarios in the future! A concrete item on the Work Zone product roadmap is the planned content federation of HTML5 application across SAP BTP subaccounts which will also rely on this direct integration setup with IAS.
Additional Read
To learn more about the topics covered in this blog post, please also refer to the following assets & follow us on SAP community.
- Discovery Center Mission: Getting Started with SAP BTP - Cloud Identity Service Provider (SAP IdP)
- Learning Journey & Certification: Implement and Administer SAP Build Work Zone | SAP Learning
- SAP Help guides for more details:
- Post Booster Configuration | SAP Help Portal (advanced) & Post Booster Configuration | SAP Help Portal (SuccessFactors)
- User Authentication, Provisioning and Authorization | SAP Help Portal
- CIO Guide: Identity Lifecycle in Hybrid Landscapes (sap.com)
Labels:
5 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels in this area
-
ABAP CDS Views - CDC (Change Data Capture)
2 -
AI
1 -
Analyze Workload Data
1 -
BTP
1 -
Business and IT Integration
2 -
Business application stu
1 -
Business Technology Platform
1 -
Business Trends
1,658 -
Business Trends
109 -
CAP
1 -
cf
1 -
Cloud Foundry
1 -
Confluent
1 -
Customer COE Basics and Fundamentals
1 -
Customer COE Latest and Greatest
3 -
Customer Data Browser app
1 -
Data Analysis Tool
1 -
data migration
1 -
data transfer
1 -
Datasphere
2 -
Event Information
1,400 -
Event Information
74 -
Expert
1 -
Expert Insights
177 -
Expert Insights
346 -
General
1 -
Google cloud
1 -
Google Next'24
1 -
GraphQL
1 -
Kafka
1 -
Life at SAP
780 -
Life at SAP
14 -
Migrate your Data App
1 -
MTA
1 -
Network Performance Analysis
1 -
NodeJS
1 -
PDF
1 -
POC
1 -
Product Updates
4,575 -
Product Updates
388 -
Replication Flow
1 -
REST API
1 -
RisewithSAP
1 -
SAP BTP
1 -
SAP BTP Cloud Foundry
1 -
SAP Cloud ALM
1 -
SAP Cloud Application Programming Model
1 -
SAP Datasphere
2 -
SAP S4HANA Cloud
1 -
SAP S4HANA Migration Cockpit
1 -
Technology Updates
6,871 -
Technology Updates
479 -
Workload Fluctuations
1
Related Content
- Your Ultimate Guide for SAP Sapphire 2024 Orlando in Technology Blogs by SAP
- First steps to work with SAP Cloud ALM Deployment scenario for SAP ABAP systems (7.40 or higher) in Technology Blogs by SAP
- How to Install SAP Cloud Connector on a Mac M2 chipset in Technology Q&A
- How to Install SAP Cloud Connector on a Mac M2 Processor in Technology Q&A
- Automated check for SAP HANA Cloud availability with SAP Automation Pilot in Technology Blogs by SAP
Top kudoed authors
| User | Count |
|---|---|
| 17 | |
| 15 | |
| 12 | |
| 11 | |
| 9 | |
| 8 | |
| 8 | |
| 7 | |
| 7 | |
| 7 |