- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- Explore Business Continuity Options for SAP worklo...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction:
To handle disasters due to natural events (like floods, earthquake etc..), power outages, application outages, accidental data loss due to human errors, Business Continuity Planning (BCP) is part of every customer`s IT strategy. Disaster recovery is a key element of BCP & is critical for organizations running mission critical workloads such as SAP. However, managing disaster recovery on-premises is cost, time and resource intensive. They can also be complex to implement and test.
AWS Elastic Disaster Recovery (also known as DRS) can help to mitigate this aspect without compromising the reliability of your applications.
AWS Elastic Disaster Recovery simplifies and automates disaster recovery by leveraging AWS as a scalable and cost-effective recovery site for your on-premises and cloud-based applications. You can quickly recover your on-premises and cloud-based SAP applications using AWS Elastic Disaster Recovery. It reduces costs by removing idle recovery site resources, and you pay for your fully provisioned disaster recovery site on AWS only when you need it for recovery or drills.
For SAP workloads already running on AWS, you can use AWS Elastic Disaster Recovery to recover applications in another AWS Region, which can help you meet resilience and availability goals for these applications.
In this blog post we will walk you through the key benefits, features, disaster recovery scenarios & lessons learned from our internal POC for failover & failback of SAP workloads using AWS Elastic Disaster Recovery service.
Key benefits and features:
AWS DRS is application agnostics and replicate data at the block level.
Key benefits and features are:
Flexible:
AWS DRS is easy to setup & configure. You can recover any on-premises or cloud-based source applications that runs on supported operating systems and common databases (SQL, Oracle, etc.), mission-critical applications such as SAP, and homegrown applications, hence making it adaptable to your specific needs.
Elastic Disaster Recovery automatically provisions and manages a staging area subnet. The subnet uses cost-effective AWS resources to receive your replicated data to help limit incurring significant costs.
Reliable:
DRS continuously replicates your workloads at the block level in a reliable and robust manner, Continuous replication can help you meet desired RPOs and RTOs related SLAs.
For events like ransomware attacks, data corruption, accidental user error, or bad patches, you can use DRS to recover your servers on AWS from a previous point in time.
Simple & highly automated:
You need only minimal skills to set up and operate Elastic Disaster Recovery. There is a streamlined, unified process to test, recover, and fail back all your applications to AWS.
You can also conduct frequent, nondisruptive drills at any time to help maintain disaster readiness.
Pre-Requisites:
To use AWS Elastic Disaster Recovery, the service must first be initialized for any AWS Region in which you plan to use Elastic Disaster Recovery.
In your AWS account where you want to set up disaster recovery, make sure to create VPCs for staging area and recovery area. In those VPCs, create staging area and recovery area subnets respectively.
For this POC we have created 2 IAM users.
- DRSAgentUser: AWSElasticDisasterRecoveryAgentInstallationPolicy
- Failback: AWSElasticDisasterRecoveryFailbackInstallationPolicy
Security groups: If the default group is too open, you can apply a different security group with relevant rules and uncheck the default security group. Note that an incorrectly configured security group could result in replication being unable to function.
Supported operating systems: With AWS Elastic Disaster Recovery, you can replicate your on-premises, virtual or cloud-based servers to variety of operating systems. For the entire list and additional considerations, refer supported operating systems documentation on AWS portal. Please refer the URL below for supported operating systems.
To prepare your network for running Elastic Disaster Recovery, open below Firewall ports:
- Source servers and the replication servers launched by AWS Elastic Disaster Recovery in your staging area subnet need to be able to send data over TCP port 443 to the AWS Elastic Disaster Recovery API endpoint.
- The source servers on which the AWS Replication Agent is installed need be able to send data over TCP port 1500 to the Replication Servers in the staging area subnet.
Make sure to check system settings on source servers:
- Root directory – Verify that your source server has at least 4 GB of free disk space on the root directory (/)
- RAM – Verify that your source server has at least 300 MB of free RAM to run the AWS Replication Agent.
- Python is installed on the server – Python 2 (2.4 or above) or Python 3 (3.0 or above).
- Free disk space on the /tmp directory – for the duration of the installation process only, verify that you have at least 500 MB of free disk space on the /tmp directory.
- The active bootloader software is GRUB 1 or 2.
- Ensure that /tmp is mounted as read+write+exec.
- Root user access
- Ensure that the dhclient package is installed.
- Verify that you have kernel-devel/linux-headers installed that are the same version as the kernel you are running.
Scenarios:
Below are the architecture diagrams of scenarios we tested for POC.
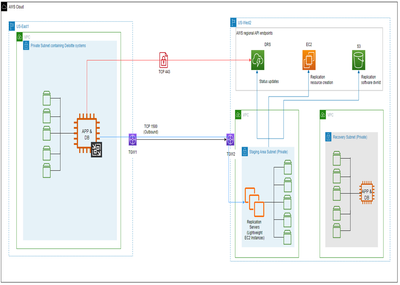
Scenario1: Cross-region
Both the application and database are on same source server and replicated using DRS
In this scenario, SAP workload is running in us-east-1 region. Failover was tested in us-west-2 region using AWS Elastic Disaster Recovery (EDR) service.
Before the actual failover, we performed failover drill.
After the actual failover to the us-west-2 region, we accessed the SAP system from the RDP host (windows server) & performed required SAP application testing and validations.
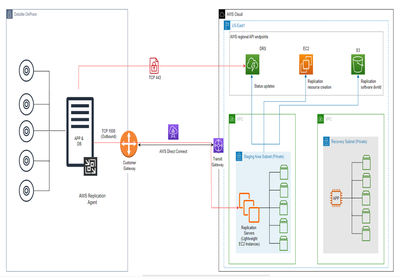
Scenario 2: On-premises Source
Both the application and database are on same source server and replicated using DRS
In this scenario we tested the failover of SAP workload running on-premises using AWS EDR service. DR site is AWS us-east-1 region.
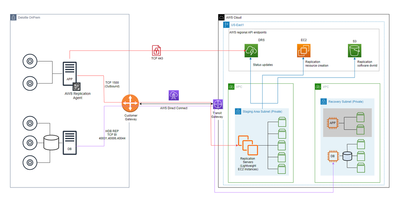
Scenario 3: On-premises Source distributed.
Database server is different from application server and replicated using HSR replication and Application is replicated using DRS.
In this scenario, SAP workload running on-premises. SAP application and databases are running on distributed hosts. HANA database is replicated to DR site (us-east-1) using SAP HANA System Replication (HSR). SAP application is replicated using AWS EDR.
Steps to set up DR using DRS:
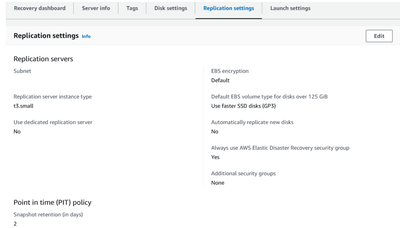
Set up replication servers:
- They should be set up in the region where you want to perform the DRS.
- These default settings will be applied to every source server that is added to AWS Elastic Disaster Recovery. However, you can change them later individually.
- Choose Set default replication settings on the AWS Elastic Disaster Recovery landing page.
- Choose the subnet within which the replication server will be launched.
- Replication server instance type (the default is a t3. small)
Specify volumes and security groups:
- Amazon EBS volume type is an important section. Any source drive less than 500 GiB in size will be selected as the standard volume type, which is a low-cost Amazon EBS volume. Any volume greater than 500 GiB can be a faster, general purpose gp2 volume or a slower but far cheaper st1 volume. If your source drives are not I/O intensive in nature, the cheaper option might suit you. However, if your source is quite busy, consider the faster volumes to avoid Amazon EBS becoming a bottleneck in your replication. You can then decide if your replication server EBS volumes should be encrypted at rest. If you want them to be encrypted, you can decide to use the default key for Amazon EBS encryption. You can also use a customer-managed key, or CMK.
- Our Source drives are greater than 500GB but not I/O intensive, so we proceeded with default selection.
- Select the custom security group that opens inbound TCP Port 1500 for receiving the data from the source servers.
Configure additional replication settings:
- By default, the AWS Replication Agent installed on your source server will attempt to communicate with the replication server through its public IP. Alternatively, if you have private IP connectivity to AWS, such as through a VPN or AWS Direct Connect, you can set up communication through a private IP instead. [Note: in our case we used AWS Direct Connect]
- You can also throttle network bandwidth. By default, data replication will attempt to use all available network bandwidth, but this can be limited if needed. The throttling value is in megabits per second.
- The replication settings also include the point-in-time snapshot policy. By default, Elastic Disaster Recovery will maintain 7 days of point-in-time snapshots for each of your source servers. You can modify the days of retention based on your own requirements.
- You can edit the replication settings for each individual source servers.
Launch Settings:
Set default DRS launch settings, you can change a variety of options in General launch settings, including:
- Instance type right sizing.
- Start instance upon launch.
- Copy private IP.
- Transfer server tags
- OS licensing.
Set default EC2 launch template.
- The default EC2 launch template sets the default values that will be copied to EC2 templates created for newly added source servers. This template defines how drill, recovery, or failback instances are launched.
- We kept the default settings here, as we wanted to configure launch templates individually for every source server.
Adding source servers:
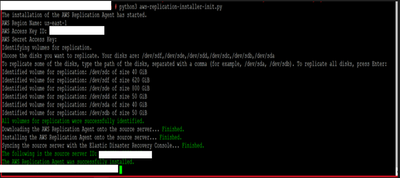
- Download the agent installer aws-replication-installer-init.py onto your Linux source server.
- Ex: wget -O ./aws-replication-installer-init.py https://aws-elastic-disaster-recovery-us-east-1.s3.us-east-1.amazonaws.com/latest/linux/aws-replicat...
- run the installation script. [sudo python3 aws-replication-installer-init.py]
- Enter your AWS Region Name, the AWS Access Key ID and AWS Secret Access Key that you previously generated.
- Choose the disks you want to replicate; press enter if you want to replicate all disks.
- Now, you can see the real time progress on source server’s page. It will take time to complete the initial sync.
Drill/Test
Configuring launch settings:
- After you have added your source servers to the AWS Elastic Disaster Recovery console, you will need to configure the launch settings for each server which determine how your drill and recovery instances are launched in AWS.
- You must configure the launch settings prior to launching test or recovery instances based on the requirement for each source server.
- Instance type right sizing INACTIVE. Here, we selected inactive because the AWS DRS was picking an instance type automatically based on the settings in 5.1, which was much larger and expensive than what was required. And now AWS Elastic Disaster Recovery will launch the AWS instance type as configured in your EC2 launch template.
- EC2 launch template, are automatically created every time you add a source server to AWS Elastic Disaster Recovery
- Change the settings as required and make it as the default version to be used.
- Once the launch settings are done, set a default launch template for the instances.
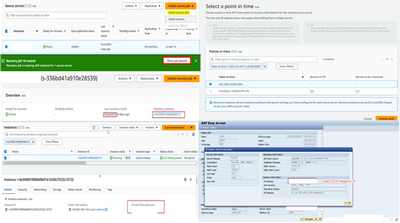
Launching a drill instance:
- After you have added all your source servers and configured their launch settings, you are ready to launch a drill instance.
- Once the status is ready, proceed to initiate recovery drill.
- Select the Point in Time snapshot from which to launch the instances for the selected source server à Initiate drill.
- The AWS Elastic Disaster Recovery Console will indicate Recovery job is creating drill instance for X source servers when the drill has started.
- Once the recovery job is successful, you will see the recovery instance ID.
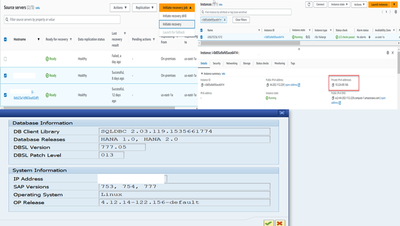
- Test the launched drill instance from both OS and SAP GUI level
Actual Failover
- Once you have finalized the testing of source server, you are ready for recovery.
- Make the source server down to initiate recovery.
- Select the source servers and initiate recovery and follow the same process as of a drill instance.
Failback
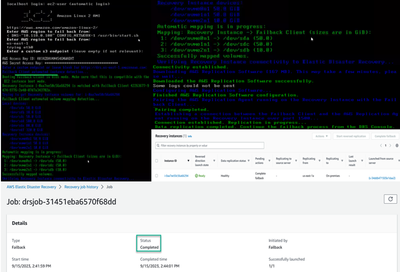
- Once the disaster is over, you can perform a failback to your original source server or to any other AWS Elastic Disaster Recovery Failback Client on the server.
- perform a failback from AWS server back to our on-premises server.
- To start the failback process we need to boot a failback ISO image in bios mode in on-premises.
- Using the Failback Client: Failback replication is performed by booting the Failback Client on the source server into which you want to replicate your data from AWS. To use the Failback Client, you must meet the failback prerequisites and generate failback AWS credentials as described in failback prerequisites section of the AWS DRS guide
- The AWS Elastic Disaster Recovery (DRS) Console allows you to track the progress of your failback replication on the Recovery instances.
- Post failback, restart the OS of your source server and proceed with validations.
Lessons Learned/ Best practices:
- While installing the Replication agent it failed because agent unable to add the newly created "aws-replication" user to "sudoers", upon checking OS level and found that the sudoers is getting reset and the user is not able to perform sudo commands anymore, worked with Security team and added 'aws-replication' user to be part of sudoers manually on all the source servers to overcome the issue.
- To access SAP application using SAP GUI at the recovery site, please make sure appropriate firewall ports are open & security group rules are added to the instance VPC. For ports and network setup details refer network requirements documentation.
- During our test we observed that recovery instance IP is not getting added to the /etc/hosts file by default, make sure to check and add the entries to the file.
- Later, to test the recovery instance, we launched a free-tier windows terminal and were able to launch the SAP GUI application successfully.
- At the time of our testing, cross-account failover was not supported by Amazon EDR service. Based on the feedback, this feature is now made available by AWS & is generally available to all customers and partners.
- For the recovery phase, AWS DRS provides options to recover your entire environment or a specific server or servers. Select a recovery point from which to launch servers, using their latest state or a previous point in time.
- After you have failed over to AWS, evaluate whether to continue operating your workload as primary on AWS or whether to fail back to your original source. If you choose to fail back, start replicating your data back to your original source environment as soon as it is back online. Choose whether to replicate back to the original servers or new servers, and whether to replicate only the data volumes or the entire server. For more details
The above observations are based on our POC, for the detailed troubleshooting guidance, refer AWS DRS troubleshooting guide.
Conclusion
With AWS Elastic Disaster Recovery (DRS) service organizations can setup disaster recovery sites in AWS cloud to meet their RTO and RPO requirements. It minimizes downtime and data loss with fast, reliable recovery of on-premises and cloud-based applications using affordable storage, minimal compute, and point-in-time recovery.
In this blogpost we shared the information based on our POC with different scenarios listed above. The steps & lesson learned above are purely based on POC environment setup internally, the results can significantly vary for your disaster recovery setup, depending on your specific needs of RTO and RPO. For complete details about Elastic Disaster Recovery, please refer AWS documentation AWS Elastic Disaster Recovery user guide & Disaster recovery for SAP workloads on AWS using AWS Elastic Disaster Recovery
- SAP Managed Tags:
- SAP Community
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
"TypeScript" "Development" "FeedBack"
1 -
505 Technology Updates 53
1 -
ABAP
14 -
ABAP API
1 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
3 -
ABAP Development
5 -
ABAP in Eclipse
1 -
ABAP Platform Trial
1 -
ABAP Programming
2 -
abap technical
1 -
abapGit
1 -
absl
2 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
2 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
Advanced formula
1 -
AEM
1 -
AI
8 -
AI Launchpad
1 -
AI Projects
1 -
AIML
9 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytic Models
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
4 -
API Call
2 -
API security
1 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
5 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
AS Java
1 -
ASE
1 -
ASR
2 -
ASUG
1 -
Attachments
1 -
Authentication
1 -
Authorisations
1 -
Automating Processes
1 -
Automation
2 -
aws
2 -
Azure
2 -
Azure AI Studio
1 -
Azure API Center
1 -
Azure API Management
1 -
B2B Integration
1 -
Backorder Processing
1 -
Backpropagation
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
Bank Communication Management
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
BI
1 -
bitcoin
1 -
Blockchain
3 -
bodl
1 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
14 -
BTP AI Launchpad
1 -
BTP Destination
2 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Application Studio
1 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
2 -
Business Data Fabric
3 -
Business Fabric
1 -
Business Partner
12 -
Business Partner Master Data
10 -
Business Technology Platform
2 -
Business Trends
4 -
BW4HANA
1 -
CA
1 -
calculation view
1 -
CAP
4 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
12 -
CDS
2 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
chatgpt
3 -
CICD
1 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
1 -
Cloud Extensibility
1 -
Cloud Foundry
4 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation
1 -
Consolidation Extension for SAP Analytics Cloud
3 -
Control Indicators.
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Cosine similarity
1 -
CPI
1 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Custom Headers
1 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
cyber security
4 -
cybersecurity
1 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analytics
2 -
Data and Analytics (DA)
1 -
Data Archiving
1 -
Data Back-up
1 -
Data Flow
1 -
Data Governance
5 -
Data Integration
2 -
Data Quality
12 -
Data Quality Management
12 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
8 -
Database and Data Management
1 -
database tables
1 -
Databricks
1 -
Dataframe
1 -
Datasphere
3 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debugging
2 -
Defender
1 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
1 -
Devops
1 -
digital transformation
1 -
Disaster Recovery
1 -
Documentation
1 -
Dot Product
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT ABAP Development Tools
2 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
1 -
Entra
1 -
ESLint
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
2 -
Exploits
1 -
Fiori
15 -
Fiori Elements
2 -
Fiori SAPUI5
12 -
first-guidance
1 -
Flask
2 -
FTC
1 -
Full Stack
8 -
Funds Management
1 -
gCTS
1 -
GenAI hub
1 -
General
2 -
Generative AI
1 -
Getting Started
1 -
GitHub
10 -
Google cloud
1 -
Grants Management
1 -
groovy
2 -
GTP
1 -
HANA
6 -
HANA Cloud
2 -
Hana Cloud Database Integration
2 -
HANA DB
2 -
Hana Vector Engine
1 -
HANA XS Advanced
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
8 -
HTML5 Application
1 -
Identity cards validation
1 -
idm
1 -
Implementation
1 -
Infuse AI
1 -
input parameter
1 -
instant payments
1 -
Integration
3 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
iot
1 -
Java
1 -
JMS Receiver channel ping issue
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kerberos for ABAP
9 -
Kerberos for JAVA
8 -
KNN
1 -
Launch Wizard
1 -
Learning Content
2 -
Life at SAP
5 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
Loading Indicator
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
4 -
Marketing
1 -
Master Data
3 -
Master Data Management
14 -
Maxdb
2 -
MDG
1 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
5 -
ML Model Development
1 -
MLFlow
1 -
Modeling in SAP HANA Cloud
8 -
Monitoring
3 -
MPL
1 -
MTA
1 -
Multi-factor-authentication
1 -
Multi-Record Scenarios
1 -
Multilayer Perceptron
1 -
Multiple Event Triggers
1 -
Myself Transformation
1 -
Neo
1 -
Neural Networks
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
3 -
ODATA
2 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
Onpremise
1 -
open source
2 -
OpenAI API
1 -
Oracle
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
Partner Built Foundation Model
1 -
PAS-C01
1 -
Pay Component Management
1 -
PGP
1 -
Pickle
1 -
PLANNING ARCHITECTURE
1 -
Popup in Sap analytical cloud
1 -
PostgrSQL
1 -
POSTMAN
1 -
Prettier
1 -
Process Automation
2 -
Product Updates
6 -
PSM
1 -
Public Cloud
1 -
Python
5 -
python library - Document information extraction service
1 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
React
1 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
research
1 -
Resilience
1 -
REST
1 -
REST API
1 -
Retagging Required
1 -
Risk
1 -
rolandkramer
2 -
Rolling Kernel Switch
1 -
route
1 -
rules
1 -
S4 HANA
1 -
S4 HANA Cloud
1 -
S4 HANA On-Premise
1 -
S4HANA
4 -
S4HANA Cloud
1 -
S4HANA_OP_2023
2 -
SAC
10 -
SAC PLANNING
9 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
1 -
SAP AI Core
9 -
SAP AI Launchpad
8 -
SAP Analytic Cloud
1 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
5 -
SAP Analytics Cloud for Consolidation
3 -
SAP Analytics cloud planning
1 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP API Management
1 -
SAP Application Logging Service
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BO FC migration
1 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BODS migration
1 -
SAP BPC migration
1 -
SAP BTP
24 -
SAP BTP Build Work Zone
2 -
SAP BTP Cloud Foundry
8 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Generative AI
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP BTPEA
1 -
SAP Build
11 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
3 -
SAP Build work zone
10 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
1 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP CDS VIEW
1 -
SAP Certification
1 -
SAP Cloud ALM
4 -
SAP Cloud Application Programming Model
1 -
SAP Cloud Integration
1 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
8 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
2 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
9 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
3 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HANA PAL
1 -
SAP HANA Vector
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
10 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP LAGGING AND SLOW
1 -
SAP Learning Class
1 -
SAP Learning Hub
1 -
SAP Master Data
1 -
SAP Odata
2 -
SAP on Azure
2 -
SAP PAL
1 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP Prepackaged Content
1 -
sap print
1 -
SAP Process Automation
2 -
SAP Process Integration
2 -
SAP Process Orchestration
1 -
SAP Router
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
2 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP successfactors
3 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP Utilities
1 -
SAP-GUI
8 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapfirstguidance
3 -
SAPHANAService
1 -
SAPIQ
2 -
sapmentors
1 -
saponaws
2 -
saprouter
1 -
SAPRouter installation
1 -
SAPS4HANA
1 -
SAPUI5
5 -
schedule
1 -
Script Operator
1 -
Secure Login Client Setup
8 -
security
9 -
Selenium Testing
1 -
Self Transformation
1 -
Self-Transformation
1 -
SEN
1 -
SEN Manager
1 -
Sender
1 -
service
2 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
8 -
Singlesource
1 -
SKLearn
1 -
Slow loading
1 -
SOAP
2 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
1 -
sql script
1 -
SSL
8 -
SSO
8 -
Story2
1 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Platform
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
Synthetic User Monitoring
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technology Updates
15 -
Technology Updates
1 -
Technology_Updates
1 -
terraform
1 -
Testing
1 -
Threats
2 -
Time Collectors
1 -
Time Off
2 -
Time Sheet
1 -
Time Sheet SAP SuccessFactors Time Tracking
1 -
Tips and tricks
2 -
toggle button
1 -
Tools
1 -
Trainings & Certifications
1 -
Transformation Flow
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
3 -
ui designer
1 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
2 -
Vector Engine
1 -
Vectorization
1 -
Visual Studio Code
1 -
VSCode
2 -
VSCode extenions
1 -
Vulnerabilities
1 -
Web SDK
1 -
Webhook
1 -
work zone
1 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
- SAP Build Process Automation Agent 3 Updates and Key Benefits in Technology Blogs by SAP
- Top 10 Technical Best Practices for Achieving 100% Customer Satisfaction in SAP Basis Services in Technology Blogs by Members
- Unlocking Data Value #1: SAP BTP Data and Analytics overview in Technology Blogs by SAP
- Business Continuity with RISE and BTP: part 2 - Technical Building Blocks in RISE in Technology Blogs by SAP
| User | Count |
|---|---|
| 54 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |