- SAP Community
- Products and Technology
- Technology
- Technology Blogs by Members
- SAP Migration to AWS - Considerations from Infrast...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction: This Blog explains few key areas in Infrastructure layer to be considered when we are planning to migrate our SAP Landscape to AWS.
Expected Readers:
- Basis Consultant with basic AWS knowledge
- SAP Basis Migration Tech Arch
- SAP Solution Architect
- SAP pre-sales team in Basis area
- Infra architect for any SAP migration assignment
Scenario:
This blog will cover below scenarios:
- SAP Brownfield Migration in AWS
- SAP Greenfield Implementation in AWS
Details:
Below are the major categories which we would need to focus on in the planning phase and have to be ready before we start with our POC/Baseline Migration. Each category provides a few options (not in every case/scenario) with pros/cons. This will help the design/architecture team to determine the right architecture for their client:
1. VPC Architecture:
This will be the 1st thing that we should check while starting our designing session as this has high impact on Architecture / Cost. Here are few options based on my experience:
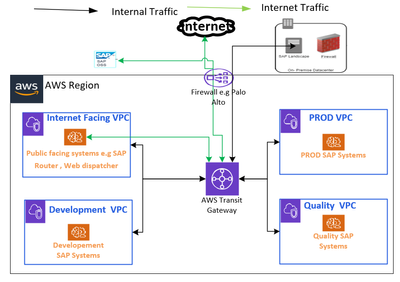
A) Complete Segregation of Landscape: This scenario explains SAP Dev, QA, PROD are in private separate VPCs. Web-facing systems like web dispatcher, SAP routers will be in web-facing public VPCs & DR DB nodes/applications EC2 will be in another DR VPC. We can use Development, QA, and PROD account for building the same.
Pros:
- We can have complete segregation of firewall, security policy which can help to determine the cost of different landscape / VPCs.
- Separating Web VPCs will allow us further safeguarding our Core SAP systems.
- Before going for PROD migration , we can test all internal & external connectivity in Dev , QA and Non PROD Web VPCs.
- Lesser operational overhead for managing Security Groups as we can define common SGs through out VPC and will get assign while provisioning EC2.
Cons: This might have a bit of impact on cost. As we know we have transit gateway between every VPCs and any transit via transit gateway will have cost impact.
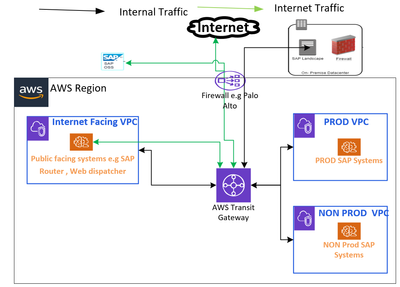
B) Shared VPCs between Non PROD and PROD : This means we can share our non-production systems in one VPC, production in another VPC & web facing applications like SAP router, web dispatcher in one common VPCs. In this option, we can put our DR DB nodes in non-PROD VPCs only.
Pros :
- We can have complete segregation of firewall, security policy between Production & Non Production SAP systems.
- Separating Web VPCs will allow us further safeguarding our Core SAP systems.
- Before going for PROD migration , we can test all internal & external connectivity in Non PROD VPCs.
- Cost effective comparing to Option A.
Cons :
Will not been able to make complete segregation between Development and QA landscape w.r.t firewall / security policy.
Overhead on maintaining separate policy on SGs to be assign in Dev landscape Vs QA Landscape.
NOTE : We need to select our CIDR range based on the number of Ips we are anticipating in each option.
2. External Traffic and Load balancing : As per my experience, this topic was somehow not fully discussed/aligned when we start our migration and become a challenge as we proceeded further with migration. Hence, strongly recommending discussing and closing it during planning session. Let me try and explain a few scenarios here based on my experience:
A. Using same On prem F5 for managing External traffic & load balancing : In this scenario we need to update the existing F5 iRule with the AWS server details to navigate the traffic towards SAP. In most of the cases I see, the backend destination for F5 will be the SAP web dispatcher which will stay in web facing VPC (for some scenarios where we don’t have a web dispatcher like BOBJ, connections will go directly to BOBJ Tomcat server).
Considerations / Assumption / High level steps :
- No migration of iRules and no change of public IP since we are using the same F5.
- No extra licensing cost.
- We still need to have operational cost for maintaining the infra of F5 in on-prem.
- Steps for allowing incoming connection from on-prem F5 to web facing F5.
B. Using separate F5 for managing External traffic & load balancing : In this scenario , client wanted to completely decommission their on premise data center but wanted to continue with F5.
Considerations / Assumption / High level steps :
1. Complete removal of on-prem data center cost; however, there will be implementation effort for migration of the iRules from on-prem F5 to new F5 and updating the backend destination to AWS servers.
2. New Public IP will need to be generated which will need to be shared with all external vendors for whitelisting.
3. Steps for allowing incoming connection from on-prem F5 to web facing F5.
4. We should be very clear on SSL termination, and in case SSL is getting terminated at the F5 level, we have to import the necessary certificate from the old F5.
C. Using AWS Inhouse functionality to manage External traffic & load balancing : Well, this is a very interesting option where we can use AWS native tools like NLB / ALB for managing external traffic and the same can be used for load balancing as well.
Considerations / Assumption / High level steps:
- Complete removal of on-prem cost or F5 license cost where all the iRules of F5 need to be analyzed and implemented in NLB / ALB.
- This needs to be implemented in the web-facing public VPC with the backend as SAP web dispatcher.
- We should be very clear on SSL termination and in case SSL needs to be terminated in ALB, we have to import necessary certificates.
- Less cost-effective compared to other options.
- I strongly recommend exploring all the existing iRules with the infra-architect. In my experience, if we have a very complete path/port-based routing in F5, that might not be supported in AWS NLB/ALB.
3. Encryption to be Used for EBS: This item looks to be very simple and standard however if its not finalized and freeze , we might face challenges in later stage. In general AWS provided 3 option on encryption of EBS i.e
- AWS Managed KMS key
- Customer Managed KMS Key
The infra-architect should discuss this during the design session and close it, as once we provision EC2/start our migration, it would be difficult to change the options at the later stage.
4. Default Idle Timeout of AWS Gateway Load Balancer: To explain this , I am assuming below most common scenarios :
- Users are connecting via VDI / Jumpbox which is part of one Public VPC
- Users are connecting via VDI or Jumpbox or directly via direct connect which is part of inhouse corporate network
- Users are connecting via VDI or Jumpbox from different Cloud Vendor like AWS
By default, all AWS VPC have a default Gateway Load Balancer idle timeout which is 350 seconds, and this is hard-coded. So, when connections are flowing across VPCs, SAP users will face very frequent session hang scenarios if the SAP work process idle time out is more than 350. In order to avoid this, I would suggest checking and reducing SAP parameter “rdisp/keepalive” to less than 350 seconds.
Another experience is when you have your BW landscape in one VPC but the source system in another VPC/on-prem. There will be an impact on full/delta load because of the setting. Please explore the following SAP Note: 1410736 - TCP/IP: setting keepalive interval, which resolve my issue.
Below Linux level keep alive parameter needs to be explored:
net.ipv4.tcp_keepalive_time = 300
net.ipv4.tcp_keepalive_intvl = 75
net.ipv4.tcp_keepalive_probes = 9
Ref : Best practices for deploying Gateway Load Balancer | Networking & Content Delivery (amazon.com)
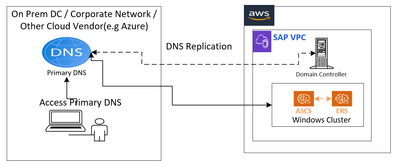
4. DNS server and its Domain Controller impact on Windows HA: It’s another item which we should finalize and agree with client. Below are a few options:
- Primary DNS in on-prem and AWS VPCs are having domain controller which will get sync with the primary DNS.
- Primary DNS is with the different cloud vendor (like Azure) whereas AWS VPCs are having domain controller which will get sync with the primary DNS.
- Primary DNS is with AWS
So, to sync any primary DNS with domain controller or vice versa, there will be a replication time, which is normally 10+ minutes. Now, if we have HA setup for windows, windows server failover cluster (popularly WSFC) will always update the ASCS / SCS node IP details directly in the DNS which is assigned to it.
For scenario 1 + 2, we should update the primary DNS details in WFSC setup as users mostly access primary detail. If we update AWS domain controller details in WSFC and a failover takes place, there might be a downtime of 10+ minutes for the users, as ASCS / SCS host details might not be synced with the primary DNS. Below picture might help to explain it in better / easy way –
5. Backup and Retention policy: There are no specific scenarios to discuss here, considering this is very generic. However, please ensure the following topics are covered and closed in the design/planning session:
- EC2 backup and retention policy and corresponding TAG details to be assigned during EC2 provisioning.
- Media to retain the backup and archiving strategy. In most cases I’ve come across, we take backups in S3 standard or S3 IA, and after a defined period we move this to Glacier for archiving.
- Depending on your database, you can decide on media, but again, in most of the cases, it will be S3. Please explore the option of using AWS native backup functionality depending on the region. Please refer this for SAP HANA blog
@ https://aws.amazon.com/about-aws/whats-new/2023/02/aws-systems-manager-sap-generally-available/
5. Time Zone sync with central NTP Server: As we aware, SAP applications always need to be in sync with server time zone. So, when we are planning to provision our EC2, we need to ensure it always gets synced with the same NTP server that on-prem servers are getting synced with.
6. Physical / Virtual Host name assignment to NIC : We mostly have both physical and virtual hostnames in our landscape. Below are the possible scenarios:
- One NIC: With this setup, we can have only one NIC where we assign the physical host to the physical IP and virtual host to virtual IP. In case we have DHCP or SSSD configuration, we will see physical hostname A record/PTR with both physical & virtual IPs.
- Multiple NIC: With this setup, we will assign one NIC to the primary hostname/IP and other NICs to other virtual hostnames/IPs. We will have a 1:1 DNS A record/PTR with this scenario.
Scenario 2 is a little more expensive than scenario 1 because of multiple NIC.
- SAP Managed Tags:
- SAP General Ledger Migration,
- SAP HANA,
- SAP Enterprise Portal, enterprise workspaces
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
"automatische backups"
1 -
"regelmäßige sicherung"
1 -
"TypeScript" "Development" "FeedBack"
1 -
505 Technology Updates 53
1 -
ABAP
14 -
ABAP API
1 -
ABAP CDS Views
2 -
ABAP CDS Views - BW Extraction
1 -
ABAP CDS Views - CDC (Change Data Capture)
1 -
ABAP class
2 -
ABAP Cloud
3 -
ABAP Development
5 -
ABAP in Eclipse
1 -
ABAP Platform Trial
1 -
ABAP Programming
2 -
abap technical
1 -
abapGit
1 -
absl
2 -
access data from SAP Datasphere directly from Snowflake
1 -
Access data from SAP datasphere to Qliksense
1 -
Accrual
1 -
action
1 -
adapter modules
1 -
Addon
1 -
Adobe Document Services
1 -
ADS
1 -
ADS Config
1 -
ADS with ABAP
1 -
ADS with Java
1 -
ADT
2 -
Advance Shipping and Receiving
1 -
Advanced Event Mesh
3 -
Advanced formula
1 -
AEM
1 -
AI
8 -
AI Launchpad
1 -
AI Projects
1 -
AIML
9 -
Alert in Sap analytical cloud
1 -
Amazon S3
1 -
Analytic Models
1 -
Analytical Dataset
1 -
Analytical Model
1 -
Analytics
1 -
Analyze Workload Data
1 -
annotations
1 -
API
1 -
API and Integration
4 -
API Call
2 -
API security
1 -
Application Architecture
1 -
Application Development
5 -
Application Development for SAP HANA Cloud
3 -
Applications and Business Processes (AP)
1 -
Artificial Intelligence
1 -
Artificial Intelligence (AI)
5 -
Artificial Intelligence (AI) 1 Business Trends 363 Business Trends 8 Digital Transformation with Cloud ERP (DT) 1 Event Information 462 Event Information 15 Expert Insights 114 Expert Insights 76 Life at SAP 418 Life at SAP 1 Product Updates 4
1 -
Artificial Intelligence (AI) blockchain Data & Analytics
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise Oil Gas IoT Exploration Production
1 -
Artificial Intelligence (AI) blockchain Data & Analytics Intelligent Enterprise sustainability responsibility esg social compliance cybersecurity risk
1 -
AS Java
1 -
ASE
1 -
ASR
2 -
ASUG
1 -
Attachments
1 -
Authentication
1 -
Authorisations
1 -
Automating Processes
1 -
Automation
2 -
aws
2 -
Azure
2 -
Azure AI Studio
1 -
Azure API Center
1 -
Azure API Management
1 -
B2B Integration
1 -
Backorder Processing
1 -
Backpropagation
1 -
Backup
1 -
Backup and Recovery
1 -
Backup schedule
1 -
BADI_MATERIAL_CHECK error message
1 -
Bank
1 -
Bank Communication Management
1 -
BAS
1 -
basis
2 -
Basis Monitoring & Tcodes with Key notes
2 -
Batch Management
1 -
BDC
1 -
Best Practice
1 -
BI
1 -
bitcoin
1 -
Blockchain
3 -
bodl
1 -
BOP in aATP
1 -
BOP Segments
1 -
BOP Strategies
1 -
BOP Variant
1 -
BPC
1 -
BPC LIVE
1 -
BTP
14 -
BTP AI Launchpad
1 -
BTP Destination
2 -
Business AI
1 -
Business and IT Integration
1 -
Business application stu
1 -
Business Application Studio
1 -
Business Architecture
1 -
Business Communication Services
1 -
Business Continuity
2 -
Business Data Fabric
3 -
Business Fabric
1 -
Business Partner
12 -
Business Partner Master Data
10 -
Business Technology Platform
2 -
Business Trends
4 -
BW4HANA
1 -
CA
1 -
calculation view
1 -
CAP
4 -
Capgemini
1 -
CAPM
1 -
Catalyst for Efficiency: Revolutionizing SAP Integration Suite with Artificial Intelligence (AI) and
1 -
CCMS
2 -
CDQ
12 -
CDS
2 -
Cental Finance
1 -
Certificates
1 -
CFL
1 -
Change Management
1 -
chatbot
1 -
chatgpt
3 -
CICD
1 -
CL_SALV_TABLE
2 -
Class Runner
1 -
Classrunner
1 -
Cloud ALM Monitoring
1 -
Cloud ALM Operations
1 -
cloud connector
1 -
Cloud Extensibility
1 -
Cloud Foundry
4 -
Cloud Integration
6 -
Cloud Platform Integration
2 -
cloudalm
1 -
communication
1 -
Compensation Information Management
1 -
Compensation Management
1 -
Compliance
1 -
Compound Employee API
1 -
Configuration
1 -
Connectors
1 -
Consolidation Extension for SAP Analytics Cloud
2 -
Control Indicators.
1 -
Controller-Service-Repository pattern
1 -
Conversion
1 -
Cosine similarity
1 -
CPI
1 -
cryptocurrency
1 -
CSI
1 -
ctms
1 -
Custom chatbot
3 -
Custom Destination Service
1 -
custom fields
1 -
Custom Headers
1 -
Customer Experience
1 -
Customer Journey
1 -
Customizing
1 -
cyber security
4 -
cybersecurity
1 -
Data
1 -
Data & Analytics
1 -
Data Aging
1 -
Data Analytics
2 -
Data and Analytics (DA)
1 -
Data Archiving
1 -
Data Back-up
1 -
Data Flow
1 -
Data Governance
5 -
Data Integration
2 -
Data Quality
12 -
Data Quality Management
12 -
Data Synchronization
1 -
data transfer
1 -
Data Unleashed
1 -
Data Value
8 -
Database and Data Management
1 -
database tables
1 -
Databricks
1 -
Dataframe
1 -
Datasphere
3 -
datenbanksicherung
1 -
dba cockpit
1 -
dbacockpit
1 -
Debugging
2 -
Defender
1 -
Delimiting Pay Components
1 -
Delta Integrations
1 -
Destination
3 -
Destination Service
1 -
Developer extensibility
1 -
Developing with SAP Integration Suite
1 -
Devops
1 -
digital transformation
1 -
Disaster Recovery
1 -
Documentation
1 -
Dot Product
1 -
DQM
1 -
dump database
1 -
dump transaction
1 -
e-Invoice
1 -
E4H Conversion
1 -
Eclipse ADT ABAP Development Tools
2 -
edoc
1 -
edocument
1 -
ELA
1 -
Embedded Consolidation
1 -
Embedding
1 -
Embeddings
1 -
Employee Central
1 -
Employee Central Payroll
1 -
Employee Central Time Off
1 -
Employee Information
1 -
Employee Rehires
1 -
Enable Now
1 -
Enable now manager
1 -
endpoint
1 -
Enhancement Request
1 -
Enterprise Architecture
1 -
Entra
1 -
ESLint
1 -
ETL Business Analytics with SAP Signavio
1 -
Euclidean distance
1 -
Event Dates
1 -
Event Driven Architecture
1 -
Event Mesh
2 -
Event Reason
1 -
EventBasedIntegration
1 -
EWM
1 -
EWM Outbound configuration
1 -
EWM-TM-Integration
1 -
Existing Event Changes
1 -
Expand
1 -
Expert
2 -
Expert Insights
2 -
Exploits
1 -
Fiori
15 -
Fiori Elements
2 -
Fiori SAPUI5
12 -
first-guidance
1 -
Flask
2 -
FTC
1 -
Full Stack
8 -
Funds Management
1 -
gCTS
1 -
GenAI hub
1 -
General
2 -
Generative AI
1 -
Getting Started
1 -
GitHub
10 -
Google cloud
1 -
Grants Management
1 -
groovy
2 -
GTP
1 -
HANA
6 -
HANA Cloud
2 -
Hana Cloud Database Integration
2 -
HANA DB
2 -
Hana Vector Engine
1 -
HANA XS Advanced
1 -
Historical Events
1 -
home labs
1 -
HowTo
1 -
HR Data Management
1 -
html5
8 -
HTML5 Application
1 -
Identity cards validation
1 -
idm
1 -
Implementation
1 -
Infuse AI
1 -
input parameter
1 -
instant payments
1 -
Integration
3 -
Integration Advisor
1 -
Integration Architecture
1 -
Integration Center
1 -
Integration Suite
1 -
intelligent enterprise
1 -
iot
1 -
Java
1 -
JMS Receiver channel ping issue
1 -
job
1 -
Job Information Changes
1 -
Job-Related Events
1 -
Job_Event_Information
1 -
joule
4 -
Journal Entries
1 -
Just Ask
1 -
Kerberos for ABAP
9 -
Kerberos for JAVA
8 -
KNN
1 -
Launch Wizard
1 -
Learning Content
2 -
Life at SAP
5 -
lightning
1 -
Linear Regression SAP HANA Cloud
1 -
Loading Indicator
1 -
local tax regulations
1 -
LP
1 -
Machine Learning
4 -
Marketing
1 -
Master Data
3 -
Master Data Management
14 -
Maxdb
2 -
MDG
1 -
MDGM
1 -
MDM
1 -
Message box.
1 -
Messages on RF Device
1 -
Microservices Architecture
1 -
Microsoft
1 -
Microsoft Universal Print
1 -
Middleware Solutions
1 -
Migration
5 -
ML Model Development
1 -
MLFlow
1 -
Modeling in SAP HANA Cloud
8 -
Monitoring
3 -
MPL
1 -
MTA
1 -
Multi-factor-authentication
1 -
Multi-Record Scenarios
1 -
Multilayer Perceptron
1 -
Multiple Event Triggers
1 -
Myself Transformation
1 -
Neo
1 -
Neural Networks
1 -
New Event Creation
1 -
New Feature
1 -
Newcomer
1 -
NodeJS
3 -
ODATA
2 -
OData APIs
1 -
odatav2
1 -
ODATAV4
1 -
ODBC
1 -
ODBC Connection
1 -
Onpremise
1 -
open source
2 -
OpenAI API
1 -
Oracle
1 -
PaPM
1 -
PaPM Dynamic Data Copy through Writer function
1 -
PaPM Remote Call
1 -
Partner Built Foundation Model
1 -
PAS-C01
1 -
Pay Component Management
1 -
PGP
1 -
Pickle
1 -
PLANNING ARCHITECTURE
1 -
Popup in Sap analytical cloud
1 -
PostgrSQL
1 -
POSTMAN
1 -
Prettier
1 -
Process Automation
2 -
Product Updates
6 -
PSM
1 -
Public Cloud
1 -
Python
5 -
python library - Document information extraction service
1 -
Qlik
1 -
Qualtrics
1 -
RAP
3 -
RAP BO
2 -
React
1 -
Record Deletion
1 -
Recovery
1 -
recurring payments
1 -
redeply
1 -
Release
1 -
Remote Consumption Model
1 -
Replication Flows
1 -
research
1 -
Resilience
1 -
REST
1 -
REST API
1 -
Retagging Required
1 -
Risk
1 -
rolandkramer
2 -
Rolling Kernel Switch
1 -
route
1 -
rules
1 -
S4 HANA
1 -
S4 HANA Cloud
1 -
S4 HANA On-Premise
1 -
S4HANA
4 -
S4HANA Cloud
1 -
S4HANA_OP_2023
2 -
SAC
10 -
SAC PLANNING
9 -
SAP
4 -
SAP ABAP
1 -
SAP Advanced Event Mesh
1 -
SAP AI Core
9 -
SAP AI Launchpad
8 -
SAP Analytic Cloud
1 -
SAP Analytic Cloud Compass
1 -
Sap Analytical Cloud
1 -
SAP Analytics Cloud
4 -
SAP Analytics Cloud for Consolidation
3 -
SAP Analytics Cloud Story
1 -
SAP analytics clouds
1 -
SAP API Management
1 -
SAP Application Logging Service
1 -
SAP BAS
1 -
SAP Basis
6 -
SAP BODS
1 -
SAP BODS certification.
1 -
SAP BODS migration
1 -
SAP BTP
24 -
SAP BTP Build Work Zone
2 -
SAP BTP Cloud Foundry
8 -
SAP BTP Costing
1 -
SAP BTP CTMS
1 -
SAP BTP Generative AI
1 -
SAP BTP Innovation
1 -
SAP BTP Migration Tool
1 -
SAP BTP SDK IOS
1 -
SAP BTPEA
1 -
SAP Build
11 -
SAP Build App
1 -
SAP Build apps
1 -
SAP Build CodeJam
1 -
SAP Build Process Automation
3 -
SAP Build work zone
10 -
SAP Business Objects Platform
1 -
SAP Business Technology
2 -
SAP Business Technology Platform (XP)
1 -
sap bw
1 -
SAP CAP
2 -
SAP CDC
1 -
SAP CDP
1 -
SAP CDS VIEW
1 -
SAP Certification
1 -
SAP Cloud ALM
4 -
SAP Cloud Application Programming Model
1 -
SAP Cloud Integration
1 -
SAP Cloud Integration for Data Services
1 -
SAP cloud platform
8 -
SAP Companion
1 -
SAP CPI
3 -
SAP CPI (Cloud Platform Integration)
2 -
SAP CPI Discover tab
1 -
sap credential store
1 -
SAP Customer Data Cloud
1 -
SAP Customer Data Platform
1 -
SAP Data Intelligence
1 -
SAP Data Migration in Retail Industry
1 -
SAP Data Services
1 -
SAP DATABASE
1 -
SAP Dataspher to Non SAP BI tools
1 -
SAP Datasphere
9 -
SAP DRC
1 -
SAP EWM
1 -
SAP Fiori
3 -
SAP Fiori App Embedding
1 -
Sap Fiori Extension Project Using BAS
1 -
SAP GRC
1 -
SAP HANA
1 -
SAP HANA PAL
1 -
SAP HANA Vector
1 -
SAP HCM (Human Capital Management)
1 -
SAP HR Solutions
1 -
SAP IDM
1 -
SAP Integration Suite
10 -
SAP Integrations
4 -
SAP iRPA
2 -
SAP LAGGING AND SLOW
1 -
SAP Learning Class
1 -
SAP Learning Hub
1 -
SAP Master Data
1 -
SAP Odata
2 -
SAP on Azure
2 -
SAP PAL
1 -
SAP PartnerEdge
1 -
sap partners
1 -
SAP Password Reset
1 -
SAP PO Migration
1 -
SAP Prepackaged Content
1 -
sap print
1 -
SAP Process Automation
2 -
SAP Process Integration
2 -
SAP Process Orchestration
1 -
SAP Router
1 -
SAP S4HANA
2 -
SAP S4HANA Cloud
2 -
SAP S4HANA Cloud for Finance
1 -
SAP S4HANA Cloud private edition
1 -
SAP Sandbox
1 -
SAP STMS
1 -
SAP successfactors
3 -
SAP SuccessFactors HXM Core
1 -
SAP Time
1 -
SAP TM
2 -
SAP Trading Partner Management
1 -
SAP UI5
1 -
SAP Upgrade
1 -
SAP Utilities
1 -
SAP-GUI
8 -
SAP_COM_0276
1 -
SAPBTP
1 -
SAPCPI
1 -
SAPEWM
1 -
sapfirstguidance
3 -
SAPHANAService
1 -
SAPIQ
2 -
sapmentors
1 -
saponaws
2 -
saprouter
1 -
SAPRouter installation
1 -
SAPS4HANA
1 -
SAPUI5
5 -
schedule
1 -
Script Operator
1 -
Secure Login Client Setup
8 -
security
9 -
Selenium Testing
1 -
Self Transformation
1 -
Self-Transformation
1 -
SEN
1 -
SEN Manager
1 -
Sender
1 -
service
2 -
SET_CELL_TYPE
1 -
SET_CELL_TYPE_COLUMN
1 -
SFTP scenario
2 -
Simplex
1 -
Single Sign On
8 -
Singlesource
1 -
SKLearn
1 -
Slow loading
1 -
SOAP
2 -
Software Development
1 -
SOLMAN
1 -
solman 7.2
2 -
Solution Manager
3 -
sp_dumpdb
1 -
sp_dumptrans
1 -
SQL
1 -
sql script
1 -
SSL
8 -
SSO
8 -
Story2
1 -
Substring function
1 -
SuccessFactors
1 -
SuccessFactors Platform
1 -
SuccessFactors Time Tracking
1 -
Sybase
1 -
Synthetic User Monitoring
1 -
system copy method
1 -
System owner
1 -
Table splitting
1 -
Tax Integration
1 -
Technical article
1 -
Technical articles
1 -
Technology Updates
15 -
Technology Updates
1 -
Technology_Updates
1 -
terraform
1 -
Testing
1 -
Threats
2 -
Time Collectors
1 -
Time Off
2 -
Time Sheet
1 -
Time Sheet SAP SuccessFactors Time Tracking
1 -
Tips and tricks
2 -
toggle button
1 -
Tools
1 -
Trainings & Certifications
1 -
Transformation Flow
1 -
Transport in SAP BODS
1 -
Transport Management
1 -
TypeScript
3 -
ui designer
1 -
unbind
1 -
Unified Customer Profile
1 -
UPB
1 -
Use of Parameters for Data Copy in PaPM
1 -
User Unlock
1 -
VA02
1 -
Validations
1 -
Vector Database
2 -
Vector Engine
1 -
Vectorization
1 -
Visual Studio Code
1 -
VSCode
2 -
VSCode extenions
1 -
Vulnerabilities
1 -
Web SDK
1 -
Webhook
1 -
work zone
1 -
workload
1 -
xsa
1 -
XSA Refresh
1
- « Previous
- Next »
- Unlock the Future of Clean Core at SAP Sapphire 2024 Orlando! in Technology Blogs by SAP
- revamped SAP First Guidance Collection in Technology Blogs by Members
- SAP BTP, Kyma Runtime internally available on SAP Converged Cloud in Technology Blogs by SAP
- Value Unlocked! How customers benefit from SAP HANA Cloud in Technology Blogs by SAP
- Identity Provisioning Documentation Joined the Family of SAP Cloud Identity Services in Technology Blogs by SAP
| User | Count |
|---|---|
| 54 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |