- SAP Community
- Groups
- Interest Groups
- Security and Compliance
- Blog Posts
- Agile, Secure, and Compliant Business Operations T...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content

By Deb Drechsel, Global Head of Employee Awareness & Enablement, Global Physical Security and Jay Thoden van Velzen, Office of the CSO, SAP Global Security & Cloud Compliance
Recently, Anahita Thoms and Thomas Saueressig published an article on SAP News that strongly resonated. It asked the question, is supply chain innovation even possible in an era of tighter regulation? The article begins:
The world is experiencing a new, tougher business environment. Trade tensions, wars, climate change, and countless other disruptions are putting the brakes on a long and steady period of globalization. Given this growing uncertainty, companies must reconfigure global supply chains to improve their resilience.
Business leaders might assume that more regulation in such a volatile environment would hinder the innovation they require most at this time. However, we will argue smart and balanced regulation can serve as a catalyst for transformation.
While the article is clearly written from the perspective of how SAP solutions can help customers weather these challenges, SAP as a global software and cloud service provider must do the same.
Resilience
The resilient survive, not necessarily the strongest. The resilient know how to withstand and recover from adverse situations, or even thrive during rapid change. Birds and mammals made it through the asteroid impact 66 million years ago. The (non-avian) dinosaurs didn’t. Darwin’s “survival of the fittest” means being better adapted to one’s immediate local environment. When that environment is changing, the fittest are those that are most adaptable. That is, those that are most resilient.
Whether in business and technology operations or in physical- and cybersecurity, resilience is increasingly a factor. Business faces an uncertain business, geopolitical, regulatory, and environmental climate. The technology cycle has sped up, and on demand cloud infrastructure and cloud-native practices like Site Reliability Engineering (SRE) stress always-on service operations.
The rise in cyber threats, in particular ransomware, is focusing security teams on detection, response, and recovery, not just on protection. The impact of security incidents drives an increase in security-related regulation. The influence of DevOps and SRE is driving innovation in cloud-native security practices to scale security and compliance in cloud services.
In SAP, cybersecurity and physical security risks are managed by SAP Global Security & Cloud Compliance, with the support of colleagues throughout the organization in various technology and business functions. The Global Physical Security team is focused on staying resilient in our organization’s ability to withstand and recover from physical attacks, cyber incidents, or natural disasters. They monitor the ever-changing global threat landscape and associated risks and adjust our strategy accordingly. The measures taken to protect physical assets, people, and unauthorized access require maintaining as well as growing a resilient mindset from our organization and all security professionals.
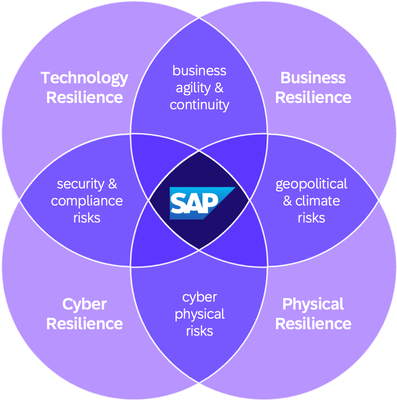
When business, technology, cyber and physical resilience align and interact – as they must, to be truly resilient – we start to see overlaps, as in the Venn diagram below. It is in these petal-shape intersections that we find opportunity. But these petals are also where gaps will appear if they are not managed well and that could make the organization vulnerable.
Resilience “Flower” Venn diagram of intersecting resilience petals
Geopolitical and Climate Risks
Business models, operations and supply chains are realigning due to the impact of trade wars and sanctions, environmental disasters and climate change, and military conflicts and political instability. Organizations may be directly affected, or indirectly through delayed delivery times or higher insurance costs. Increased regulation and reporting requirements, as mentioned in the SAP News article linked above, add an additional burden to navigate.
Protests and civic activism can add another dimension. That also goes for cloud service providers. For instance, there is growing resistance to additional data centers due to concerns regarding the environmental impact of new data centers (Chile, Portugal, The Netherlands). Data centers consume much power and water, and that is only going to increase with the growth in the use of cloud services and AI.
Business Agility and Continuity
The intersection between business and technology is how technology enables the business to respond to these geopolitical and climate risks, as well as business, financial and market risks. Technology resilience is required for business continuity – that is, keeping the lights on and recover quickly. Cloud services and cloud-native technologies such as Kubernetes have made “always-on” models viable, as well as systems that scale with demand.
Technology resilience is also required to support the necessary business agility. That means that the technology should continuously renew and be adaptable to the needs of the business, rather than hold the organization back through legacy systems and processes. Technology must be an enabler of business resilience. Business AI will contribute to that.
Security and Compliance Risks
Cybersecurity teams set policies and provide governance, but IT operations and DevOps teams must configure and operate systems according to those policies and bring them in compliance. The intersection between technology and cyber is therefore where most of the security and compliance risks lie. The gap between security requirements and the execution to those requirements is where both adversaries and auditors cause you unpleasant surprises.
DevSecOps and good Software Development Lifecycle (SDOL) practices, Continuous Integration/Continuous Delivery (CI/CD) pipelines, enforced cloud guardrails and landscape scanning all help keep that security and compliance gap small and raise resilience, without impeding the agility of technical teams.
Among the main areas of business, technology, cybersecurity and physical security, cybersecurity is the least mature. Cybersecurity leaders often still stress defense over resilience. Often repeated dogmas like “Defenders have to be right all the time, attackers only once” illustrate this, as opposed to an approach that assumes breach and focuses on detection, response, and recovery.
The rise in ransomware attacks with business impact (in terms of possible ransoms paid, loss of business, and response and recovery costs) indicates that the networks of many organizations are vulnerable. Recent reports show that is also the case for cloud landscapes. Software supply chain attacks like the Solarwinds incident pose further challenges. In reaction, governments globally are intervening with stricter regulation and are pushing more responsibility on critical infrastructure and technology providers to have processes in place to meet security baselines.
Cyber Physical Risks
The cyber-physical petal is another intersection that could jeopardize the resilience of an organization. A classic XKCD illustration (538) shows the limits of cybersecurity controls in the face of physical threats. Leaked and stolen credentials are a known issue in cybersecurity. But Multi Factor Authentication (MFA) will not protect you if a sufficiently motivated adversary forces an employee into collaboration.
Any organization with remote and office workers, and traveling executives and representatives, must consider the cybersecurity downstream effects from any physical security incidents, besides the immediate safety of those employees. Meanwhile, in the current age of virtual job interviews, hiring managers must guard against bringing adversaries into their organizations. If they don’t, they may inadvertently support a sanctioned regime.
Cybersecurity incidents in critical infrastructure and critical business systems have caused disruption of operations in resorts, cities, healthcare, fuel distribution, and global shipping. These cases show how critical resilience is in providing organizations options on how to respond and recover.
Agile, Secure and Compliant Business Operations
As we have seen, technology, cybersecurity and physical security need to act in concert to support the business to survive and thrive in the current business climate. Cloud Infrastructure-as-a-Service (IaaS) is often chosen for the agility and flexibility to scale up as well as down as needed. IaaS providers have engineered resilience into their cloud platforms, which enables their customers to configure their systems as they require. While this increases agility, it also adds the complexity of cloud infrastructure configuration in addition to managing the workloads and applications.
With Software-as-a-Service (SaaS) providers that complexity for customers is reduced to the management of the applications only. The rise of enterprise SaaS providers as documented in Acceleration Economy’s Cloud Wars suggests that customers are increasingly comfortable moving to cloud services higher up the stack.
Like all organizations, cloud service providers must be resilient. Unlike their customers, they have the benefit of what Phil Venables, CISO of Google Cloud, has called the 'decreasing marginal cost of security’. Cloud service providers can scale the cost of security and compliance controls across many landscapes and customers, and therefore can afford larger teams, and manage a broader spectrum of threats and global regulations. That also applies to SAP.
However, as a technology and service provider of enterprise business solutions, SAP is uniquely positioned among cloud companies to enable agile, secure, and compliant business operations as well as business resilience. SAP supports customers with their geopolitical and climate risks, business agility and continuity, security and compliance risks, and cyber physical risks through both its solution portfolio of applications and its cloud services operations.
Necessity is the mother of invention, as SAP experienced itself in its ongoing cloud transformation. Growing uncertainty and regulation can be a catalyst for transformation, as the SAP News article argues we began with. That article ends with three customer examples:
Necessity often drives innovation, leading companies to invest in advanced technologies […]. Unilever’s commitment to traceability and transparency in its global palm oil supply chain demonstrates how compliance acts as a transformative force. Nestlé’s embrace of technology illustrates how businesses can enhance transparency, and resiliency, while ensuring compliance with evolving standards. And Grupo Nutresa’s procurement transformation shows how it’s possible to deliver efficiencies and generate more value while doubling down on sustainability with trading partners.
SAP is honored to support customers such as these in their cloud transformation and journey towards greater resilience.
- SAP Managed Tags:
- Governance, Risk, Compliance (GRC), and Cybersecurity
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.