- SAP Community
- Products and Technology
- Human Capital Management
- HCM Blogs by SAP
- Secure your SuccessFactors to IAS/IPS integration ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
I am writing a short blog to highlight one recent change that came into effect with the latest SAP SuccessFactors Production release on December 9th, 2022. This relates specifically to Identity Authentication / Identity Provisioning so if you are working on this topic this will be relevant for you.
As of the December 9th, 2022 production release, any newly established integration between SuccessFactors BizX instance and SAP Identity Authentication/Identity Provisioning Services (IAS/IPS) will be using the X.509 certificate for authentication of integration between SuccessFactors HXM Suite and IAS/IPS instead of the previous basic authentication mechanism with just username and password. This change applies to both newly provisioned SuccessFactors BizX Instances that have an Identity Authentication and Identity Provisioning tenants bundled together and delivered at the same time, and to existing SuccessFactors BizX instances performing the Initiate IAS Upgrade or Change IAS tasks through the Upgrade Center.
What is X.509/mTLS
X.509 is an International Telecommunication Union (ITU) standard defining the format of public key certificates. X.509 certificates are used in many internet protocols, including TLS (Transport Layer Security) /SSL. Mutual Transport Layer Security (mTLS) establishes an encrypted TLS connection, in which both parties use X.509 certificates to authenticate and verify each other.
Why X.509/mTLS
mTLS prevents malicious third parties from imitating genuine applications and provides a more secure authentication option to its users.
When an application attempts to establish a connection with another application's secure web server, the mTLS protocol protects their communications, and verifies that the incoming server truly belongs to the application being called. When the client application requests access to a server application, the server application will provide its certificate to the client application and, in turn, ask the client application for its public certificate. This certificate will contain a public key, an identity, and a signature by a trusted certificate authority. Both entities will then look for the signature and climb the trust chain untill they find a mutual certificate authority validating the authenticity of both entities and creating a secure and encrypted channel.
Since both entities have to be validated, mTLS can reduce the chances of attacks, and provides a basis for zero-trust security framework, which is becoming increasingly important in cloud-based applications, and micro services deployments.
How can I find out whether I am using certificate-based authentication or basic authentication?
If your SuccessFactors BizX instance is already integrated with IAS/IPS, to find out whether you are using the previous basic authentication or the new X.509/mTLS certificate-based authentication, you can complete the following steps:
- Log into the IPS Admin Console.
- From IPS Admin console home page, click on the Source Systems tile.
- From the list of source systems, select the desired SuccessFactors tenant's record.
- Click on the Properties tab to check the value of the “authentication” parameter; if the value is BasicAuthentication, then basic authentication is used. If the value is ClientCertificateAuthentication, then X.509/mTLS certificate-based authentication is used.
Can I migrate my SF to IPS integration from basic to certificate-based authentication?
If your SuccessFactors BizX instance is already integrated with IAS/IPS and is currently using the basic authentication for communication between BizX and IAS/IPS, we recommend that you migrate to the X509/mTLS certificate-based authentication.
For steps of migration on the BizX side, please refer to our help doc.
To migrate from basic authentication to X.509/mTLS certificate-based authentication, take the following steps:
Step 1: Generate and download the certificate from IPS.
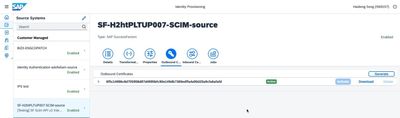
- Log into the IPS Admin Console.
- From the IPS Admin console home page, click on Source Systems tile.
- From the list of source systems, select the desired SuccessFactors tenant as the provisioning system that you want to configure client certificate authentication for.
- Select the Outbound Certificate tab and choose Generate.
- If the certificate is generated successfully, the toast message ‘Certificate generated successfully' is displayed on the screen.
- View the certificate information.
- Each certificate contains fields specifying the subject, the name of the CA issuing the certificate, the algorithm used by the issuer to sign the certificate, validity period, key size and the certificate unique identifier.
- Download the certificate.
Step 2: Register IPS for certificate-based incoming calls in BizX.
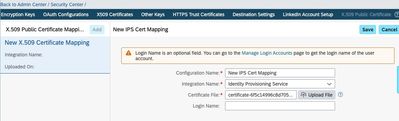
- In BizX, go to Admin Center → Security Center → X.509 Public Certificate Mapping.
- Click Add.
- Complete the following fields in the table below
- Click Save to save the changes.
Field | Description |
Configuration Name | Example: New X.509 Certificate Mapping |
Integration Name | Select the name of your application from the drop-down menu. |
Certificate File | Upload the corresponding file with a certificate file extension cer, pem, crt etc. and that follows the X.509 protocol. |
Login Name | The login name of a user that has permission to consume the SAP SuccessFactors API for its respective application. By default, a technical user would be created and used for IPS, so this field is optional and should be left blank. |
Step 3: Configure IPS to use certificate-based authentication when communicating with BizX.
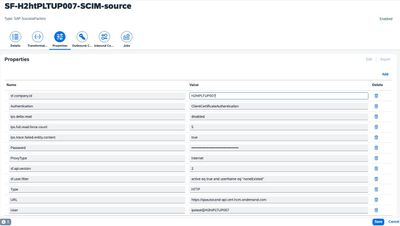
- Return to the Identity Provisioning admin console, from Source Systems, select the SF BizX tenant record, and select the Properties tab.
- Set the Authentication property to ClientCertificateAuthentication (vs "BasicAuthentication" previously using IPSADMIN, also no need to set User and Password properties)
- Set the URL parameter to the API URL with cert, for example: https://apiX.cert.sapsf.com/odata/v2
- Click Add to add a new parameter “sf.company.id” if not already available on the Properties tab, and set the value to the SuccessFactors company id corresponding to this source.
- Save your configuration.
If you are using real time user sync for new hires between BizX and IAS/IPS, then please complete the following two steps:
Step 4: Generate and download the certificate from BizX
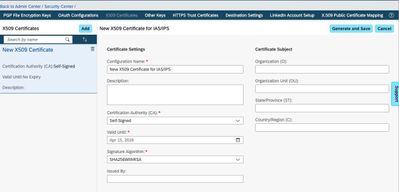
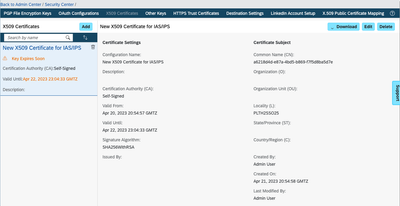
- In BizX, go to Admin Center → Security Center → X.509 Certificates:
- Click Add to add a new entry, and enter the Configuration Name and Valid Until date.
- Click Generate and Save.
- Click Download, then select X509 Certificate.
- When prompted by browser, save the file to your local file system.
Step 5: Register SF BizX as administrator in IAS using certificate.
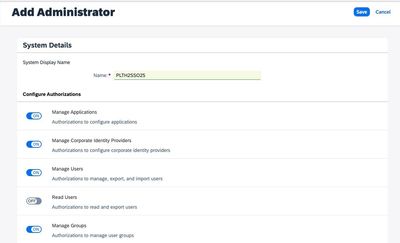
- In IAS Admin console, go to Users & Authorizations → Administrators.
- Click on Add, then select System.
- Enter the system name and click Save.
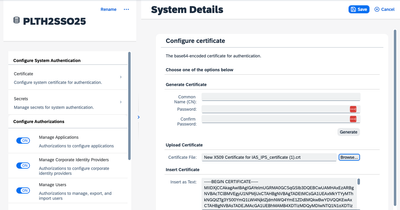
- Click on the system you just created in the previous step.
- Click on Certificate, then click Browse to find the X.509 cert file you downloaded to your local file system.
- Click Save.
- SAP Managed Tags:
- SAP Cloud Identity Services,
- SAP SuccessFactors platform,
- SAP Identity Management
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
-
1H 2023 Product Release
3 -
2H 2023 Product Release
3 -
Business Trends
104 -
Business Trends
4 -
Cross-Products
13 -
Event Information
75 -
Event Information
8 -
Events
5 -
Expert Insights
26 -
Expert Insights
21 -
Feature Highlights
16 -
Hot Topics
20 -
Innovation Alert
8 -
Leadership Insights
4 -
Life at SAP
67 -
Life at SAP
1 -
Product Advisory
5 -
Product Updates
499 -
Product Updates
44 -
Release
6 -
Technology Updates
408 -
Technology Updates
13
- Export and Import Feature of SAP SuccessFactors Talent Intelligence Hub in Human Capital Management Blogs by SAP
- 1H 2024 Release Highlights: Leveraging AI within SAP SuccessFactors Recruiting to Accelerate Hiring in Human Capital Management Blogs by SAP
- SAP SuccessFactors Talent Intelligence Hub H1 2024 Release Insights in Human Capital Management Blogs by Members
- New 1H 2024 SAP Successfactors Time (Tracking) Features in Human Capital Management Blogs by SAP
- First Half 2024 Release: What’s New for Work Tech? in Human Capital Management Blogs by SAP
| User | Count |
|---|---|
| 5 | |
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |